Focus on
what matters
All a hacker needs is just one vulnerability to get a foothold in your network.
Stay On Top Of Vulnerabilities, Locate And Prioritise Risk.
Enterprise Solutions
Make Vulnerability and Threat Management a Strategic Priority.
Don’t wait for something to happen to then quantify which vulnerability to manage first. Learn about what can connect seamlessly with your existing applications and tools.
Everything for an Enterprise organisation.
- Incorporate business risk and threat intelligence
- Comprehensive risk management system
- Reduce response time
- Clear view on vulnerability prioritisation
How to prioritise, patch or remediate identified vulnerabilities.
S4 Applications is a cybersecurity solution provider.
Incorporating emerging and market-leading technologies that protect your business, brand reputation, and your customers.
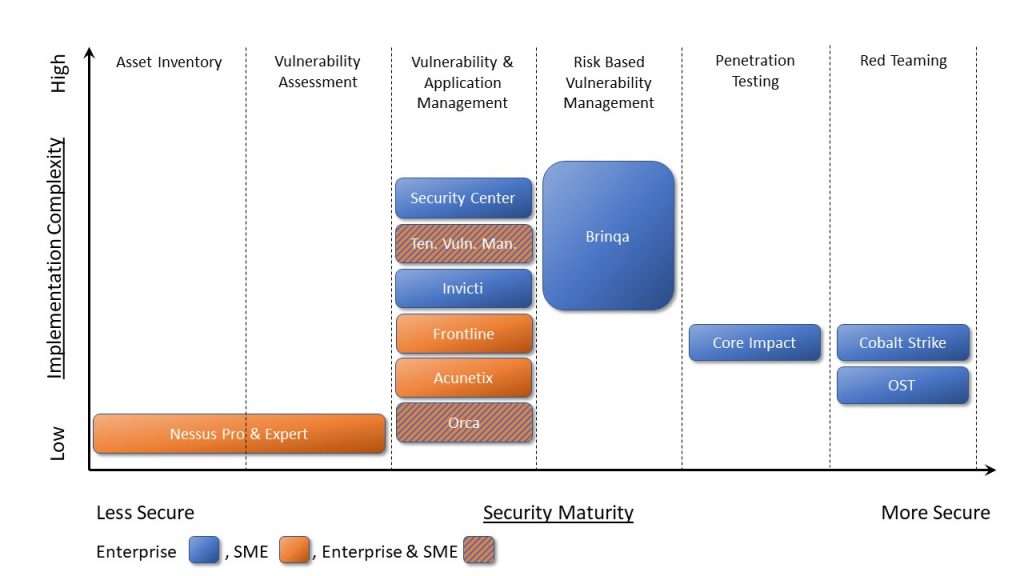
Use our 6 step maturation model to help you pinpoint your Maturity Assessment level.
SME Solutions
Combining Tech and Business Risks to Flag the Highest-Risk Vulnerabilities.
With huge growth in the number of cyber attacks you’ll need help to assess and manage what your vulnerabilities are.
SME solutions that manage risk and vulnerabilities.
- A system that is easy to deploy
- Prioritise security issues
- Easy to manage (low-intensive resources)
- Has capabilities that can be tailored and scaled if needed
- Monitor and analyse the cyber threat landscape
Incorporating emerging and market-leading technologies that protect your business, its reputation and your customers.
Pen Testing
Vulnerability Management
Threat Monitoring
Consultant Solutions
S4 Applications has the experience and access to the best Vulnerability and Exploitation tools in the market.
As a security consultant you have been tasked with assessing and flagging up critical vulnerabilities that could have a business impact.
Improve and enhance your pen testing consulting.
- Improve and upgrade pen testing
- Pinpoint and remediate security hotspots
- Tools that can be used multiple times for different clients
- Expertise in assessing security maturity and vulnerabilities by doing pen testing