Security is a journey or process, not a thing. It’s not possible to be completely “secure”, but you can become “more secure”. As an organisation goes through a security journey, it can continually improve and enhance its security posture, which it “matures”, hence “security maturity”.
What is security maturity and how can S4 Applications help you enhance your security posture?
S4 Applications has created a 6x step Cyber Security Maturity Assessment Model that helps formulate an understanding of your organisation’s current security maturity and how to enhance it (see image below).
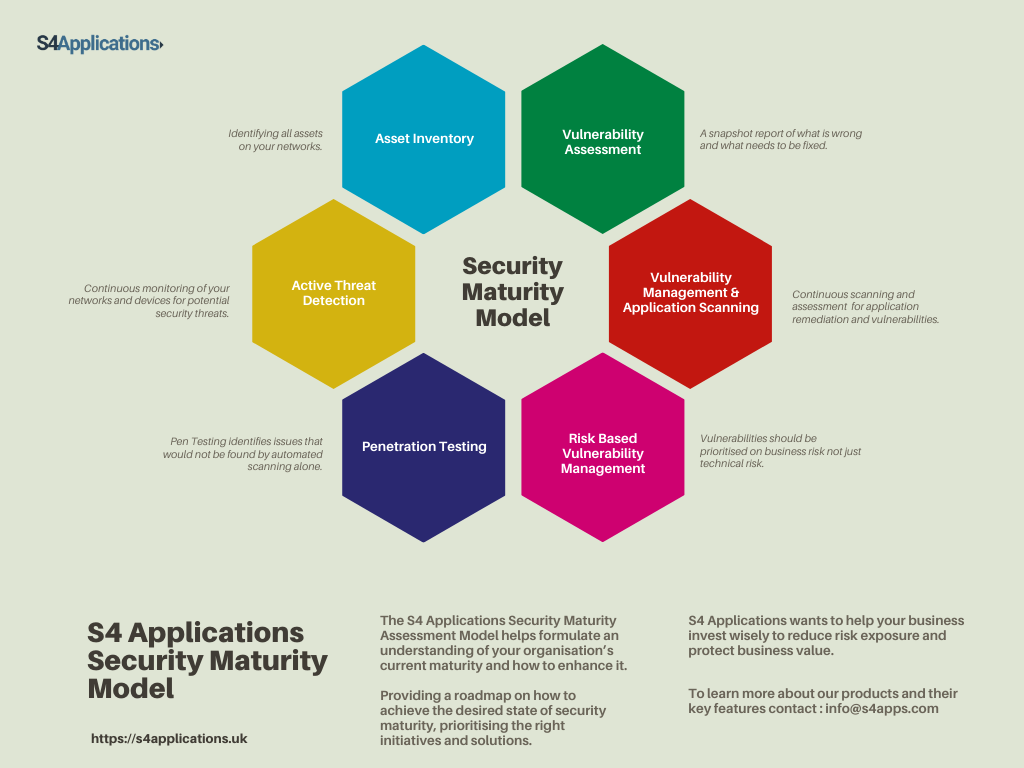
Why is Security Maturity important today, in 2020?
A data breach, a hack, downloading a virus, all can have serious consequences for a business, both financially as well as reputational.
There was a time when you could just say “ … we have a firewall so there is no way anything bad could happen to us”. Installing a firewall did make it harder to penetrate your security defences, more so than those with nothing. So, the attackers moved on to search for those businesses who were more exposed because of their vulnerabilities.
Today, nobody can ignore their security posture.
Fast forward to 2020, and the security environment businesses face today is very different. From ransomware to automated tools that scan every IP on the Internet looking for vulnerabilities to search engines like https://www.shodan.io/ that allow would be attackers to search for all the IP cameras that connect on port 12345 and similar.
So, if you have a vulnerability that is easily exploited, that is visible to the Internet – the bad news is that it has already probably been taken advantage of. In a strange quirk of fate, the attacker that exploited you, probably fixed the vulnerability in the process, to stop someone else getting in and kicking them out!!
There is so much money to be made by cyber criminals, to what many see as a “victim-less” crime.
It’s a common mistake to think your business is too small to be targeted. So, if you are careless and download a ransomware virus, it can end up being very costly. Not just in terms of your data being held hostage, or the remedial costs for clearing up the mess, but also the fact that you will lose the trust of your customers.
Many organisations struggle to comprehend the growing regulatory and compliance risks of a data leak and fail in their cyber security planning. If you have not followed the EU’s GDPR privacy regulations, it can also be an expensive fine.
Even if you have a perfect backup plan that didn’t get encrypted, the cyber criminals will have already started to exfiltrate your data as part of their processes. They take a copy of your valuable data and will release the embarrassing bits (customer contact details, emails form the CEO etc.) if you don’t pay up.
Data, data everywhere.
With so much data in circulation passing between customers, companies, partners, vendors, etc. there is always a risk of a data leak or breach, exposing confidential information.
The reasons for how data breaches happen might be traced back to a pre-meditated attack targeting a weak security perimeter. However, it can just as easily result from human error or weaknesses in a company’s information infrastructure riddled with vulnerabilities.
According to Risk Based Security, the first six months of 2019 witnessed 3,800+ publicly disclosed breaches exposing 4.1 billion compromised records, with one of the biggest data breaches in 2020 coming from Marriott hotels with over 5 million customers affected.
As companies expand and their use of data grows, staying compliant in a world where privacy regulations are everywhere can be a difficult but critical challenge to meet.
The consequences of a data breach.
According to Hiscox insurance, almost one in three (30%) of UK small businesses suffered a cyber breach – equivalent to over 4,500 successful attacks per day or one every 19 seconds.
Massive cybersecurity breaches have become commonplace from the NHS to Garmin, all regularly grabbing national headlines.
According to Accenture’s 2019 Cost of Cybercrime Study, “Humans are still the weakest link”, as human error is often the cause of exposing confidential information or accidently helping others to circumvent internal security practices.
At a time when cyber criminals are adapting to the new conditions in the market, their attack methods continue to targeting the human factor through increased ransomware, phishing and social engineering attacks to gain entry to business networks.
We all need to worry, from the sole proprietor right up to the largest Enterprise companies.
If you happen to be in a business sector perceived as being high value such as accountants, law firms, banks, financial services, and e-commerce then you have the added disadvantage that cyber criminals will devote extra time and effort to penetrate your organisation’s defences. Along with using an arsenal of automated tools to exploit known vulnerabilities.
Different levels of Security
We can define three broad areas of security, all of which apply different methods and approaches to protect your data, networks, etc.
- Defensive security
- Offensive security
- Detection
The most effective process is to start with Defensive security and work through the other security levels one-by-one.
1. Defensive security
Uses an approach to security that focuses tactics on prevention, detection, and how to withstand attacks. These tactics are performed for an organisation to avoid the risk or dangers associated with cybercrime.
Some of the following are ways to deploy a security perimeter around the organisation to deter and stop cyber-attacks:
- Fire walls – to control what can come into the organisation including VPN access
- Proxy servers – to control where you can go out
- AV / endpoint protection
- Email scanning
- Identity management
- Ensuring secure passwords & password managers
- Multi-factor authentication
- Also extend this approach to physical security – who can access the site, what is procedure to add a device to your network, etc.
2. Offensive security – where “S4 Applications are specialists”
With offensive security the objective is to think like an attacker would and view your organisation through their eyes. They will look for vulnerabilities in systems that they can use, so you should do the same.
This method exploits the security vulnerabilities found in your organisation by using pen testing and red teaming. It eliminates the guesswork of what may happen during an attack. The idea is to think like an attacker, deploying a proactive approach to security by using techniques to mimic cyber attacks.
Pen-testing is a targeted cyber-attack prevention. In simple terms, a Pen Testing consultant will think like a malicious actor and use their skill to try and gain access to your systems, documenting their findings as they penetrate your systems.
Red Teaming are an in-house team of ethical hackers continually try to by-pass your defences, keeping your detection and response teams on their toes.
Vulnerability management is the process of identifying, evaluating, treating, and reporting on security vulnerabilities in your business systems and the software that runs on them.
By using vulnerability scanners you’ll flag issues, remediate what you find, mitigate and register high risk items you cannot remediate.
Brinqa vulnerability management solutions.
S4 Applications was formed in response to businesses in EMEA looking for vulnerability assessment and remediation solutions, starting out as the only provider of Brinqa products outside of the US.
A comprehensive platform for cyber risk analysis and remediation, Brinqa helps transform threat data into insights that empower an organisation’s approach to cyber risk.
Brinqa prioritises assets, vulnerabilities, and incidents based on their impact and value to the business. So, If a vulnerability is identified across multiple machines (or applications), one on a public web site, the other internal, a typical, technical risk based approach would rate them as equally dangerous, whilst a business risk approach would focus on the public web site where the highest risk is perceived.
Read more about risk based vulnerability management with our Brinqa case studies, learn more about Brinqa or contact S4 Applications to request a demo.
3. Detection / Incident Management
If you have a large network then you have to assume that you have an attacker on the inside of your network already. If you make this assumption, how are you going to find them? Or how can you disprove it?
Some attackers could be nation state, others opportunistic, others employees who click, download and run something by mistake, and also malicious staff, say a sales person copying all of your customer data before they resign.
Assuming that the attacker has already got into your network, could be a cyber criminal, or a sales guy exporting the customer list before they resign. They will try to track down where your backups are or find and remove your high value data.
Once you find an issue you need to have a process already defined to deal with it; aka incident management. You don’t want to be making things up as you go along, you want to have thought about it beforehand, and execute that plan.
Preparation is the key to effective incident management with predetermined guidelines and a strong plan in place to support your team to prevent data loss, to look for the signs of a breach and how to manage the overall incident process.
Most companies that have a data breach that involves people (rather than some automated attack) find that the bad actor has been in the network for around 200 days on average. Read more at the Varonis Data Breach Response Times: Trends and Tips, source: Varonis.
The focus should be to monitor security events in order to detect, alert, and report on potential security incidents as bad actors may modify your logs so that there is no record of them and exfiltrate what they are after very slowly to avoid detection.
Very sophisticated companies will employ “red teams” who are tasked with hacking into the network, to replicate the same actions as a bad actor – to highlight your vulnerabilities.
Next steps
A planned and pragmatic cyber-security programme will constantly review an organisation’s current status quo. Providing a roadmap on how to achieve the desired state of security maturity, prioritising the right initiatives and solutions.
S4 Applications wants to help your business invest wisely to reduce risk exposure and protect business value. Contact us to guide you through our 6 step Maturation Model to get to grips with what your current maturity level is and prepare with you an effective plan to enhance your security maturity.

