Brinqa
Brinqa provides one platform to automate the cyber risk lifecycle across infrastructure, applications, and cloud security
Transform your Vulnerability Management with Brinqa.
Visualise, Prioritise and Remediate Cyber Risk
Risk Based Vulnerability Management.
Brinqa offers an enterprise level vulnerability and threat management solution that delivers increased risk visibility and threat intelligence, prioritised on business and technical risk to be able to focus on where the highest risk is.
Predict and prevent attacks.
Brinqa connects and synchronises siloed cybersecurity products, processes and teams. Using data to model, analyse, prioritise, remediate and report on the threat landscape, delivering a knowledge-driven and risk-centric approach.
Features:
- Automates vulnerability management
- From scan, to risk prioritisation to ticket management
- Automated from scan to ticket creation
- Seamless data integration to leverage a library of 100+ data sources
- Ensures consistent data quality across different scanners and vendors
Benefits:
- Visibility across all vulnerability risk in one place
- Faster risk identification saves time and money
- Tickets only closed when verified by scanner
- Prioritises remediation of vulnerabilities
- Improves compliance and reduces risk of fines
- Provides secure lifecycle (SDLC) governance

Get instant access today
Our comprehenise list to strengthen your businesses security today.
Brinqa Attack Surface Intelligence Platform
Leverage the full potential of your security tools
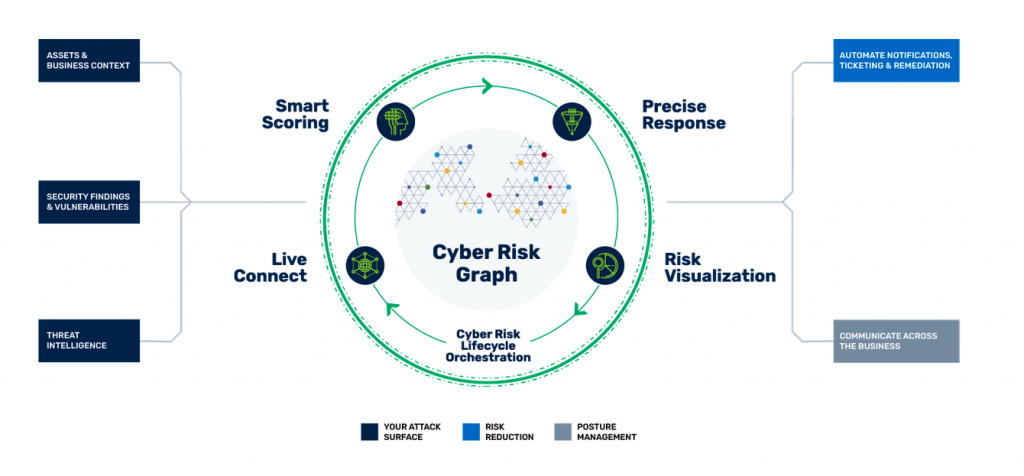
Live Connect integrates 180+ business and security tools to provide a unified inventory of assets and security findings across infrastructure, applications and cloud
- Consolidate asset views into a mega-profile that flags security control gaps
- Collect security findings and normalize vulnerability scores across security tools
- Dynamically sync to reflect changes in your attack surface
Understand your attack surface like never before
Vulnerability Risk Management
Cyber Risk Graph puts your asset and vulnerability inventory to work by adding business context and threat intel to create a live model of your attack surface.
- Understand relationships between assets, findings, controls, ownership, and threat intel
- Add business context and tribal knowledge that ensures your attack surface model reflects your business
- Cluster assets and related risk for tailored perspectives of your attack surface for all stakeholders
Next Steps - Getting Started
S4 Applications will work with your business to help you understand your attack surface, priorities, and goals and develop a roadmap to deploy the right solution for your needs.