Enterprise Vulnerability prioritisation
As an Enterprise organisation address vulnerabilities before an attacker can.
Make Vulnerability & Threat Management a Strategic Priority.

Brinqa enterprise vulnerability and threat management
Brinqa offers an enterprise level vulnerability and threat management solution that delivers increased risk visibility and threat intelligence.
- Best practice multi-dimensional risk models
- Intelligent contextualised assessments
- Automation of manual process, including ticket management
- Improve compliance - self-service
- Dynamic risk prioritisation
- Automated remediation management at scale
Orca Security provides instant-on security and compliance
Orca brings together core cloud security capabilities, including vulnerability management, compliance and more in a single, purpose-built solution for AWS, Azure, GCP, and Docker / Kubernetes.
- Simplifying cloud security operations
- Cloud security posture management
- Vulnerability management, identities, and compliance management
- Scanning database files for PII and other pattern matches
- Weak and leaked passwords
- Detecting misconfigurations
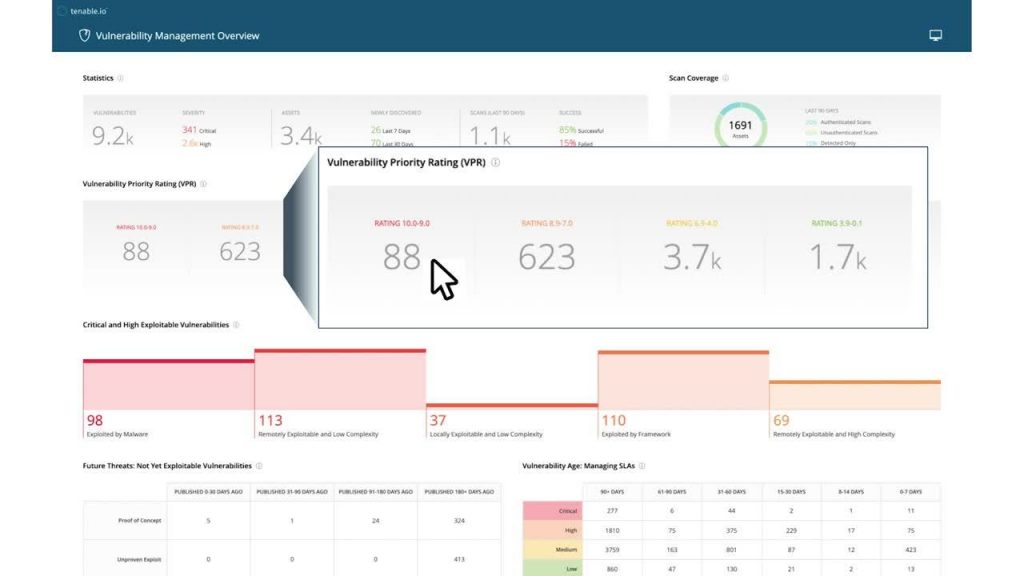
How to prioritise, patch or remediate identified vulnerabilities.
Identify, Investigate and Prioritise Assets and Vulnerabilities
Tenable Security Center on-premise solution
Tenable Security Center provides out-of-the-box, fully customisable reports and dashboards specific to leading security standards and compliance mandates.
- Leverage Tenable’s integrations with vulnerability insights.
- Improve resilience.
- Improve visibility.
- Improve speed and save money.
- improve visibility.
Tenable Vulnerability management SaaS solution
Tenable Vulnerability Management provides the actionable and accurate data you need to identify, investigate, and prioritise the remediation of vulnerabilities.
- Improve detection and save money.
- Improve speed.
- Improve visibility.
- Improve efficiency.
- Continuous monitoring of users, applications and infrastructure.
Get actionable and accurate data to identify, investigate, and prioritise vulnerabilities.

Gain threat detection solutions, monitoring malicious activity.
Outflank Security Tooling
OST is a set of private offensive security tools created by the red teaming specialists of Outflank available for use by vetted red teams.
- OST includes techniques that have not yet been published or weaponised by other red teams.
- OST tools are explicitly developed to bypass defensive measures and detection tools.
- There are tools for every phase of the attack chain.
- The toolset is under continuous development.
Cobalt Strike
Cobalt Strike replicates the tactics and techniques of an embedded advanced adversary.
- Provides post-exploitation agent and covert channels.
- Malleable C2 lets you change your network indicators to look like different malware each time.
- Unique reports designed to aid blue team training.
- Optimised to capture trust relationships and enable lateral movement with captured credentials.
Enhance and upgrade your Penetration Testing capabilities.
A web application scanner that scales for An Enterprise organisation.
Invicti
Obtain a comprehensive view of your web security posture that can be integrated within your SDLC.
Invicti doesn’t require you to have extensive IT security knowledge, a market leader that combines cutting-edge technology with an excellent user interface.
The application explains the errors causing the vulnerabilities so your security team can easily eliminate them.

- A comprehensive web security partnership programme ideal for Enterprise organisations.
- A scalable, multi-user, web application security solution.
- With built-in workflow and reporting tools.
- Automatically crawls and scans all types of legacy and modern web applications
- Offers high-level reports for management and detailed reports for your IT personnel
Maturation Model
What are your biggest risks? What are your regulatory and compliance obligations? Where should you focus your efforts?