Financial services - putting a cost on risk
Financial Services companies are constant targets for malware, ransomware and sophisticated cyber attacks.
Financial services
Reducing the attack surface for Financial Services businesses is a top priority, with a focus on correlating vulnerability, threat intelligence and asset data from multiple sources to accurately prioritise where to focus. At the same time keeping all stakeholders in the loop through KPI’s, reports and dashboards is an essential way to keep your business protected.
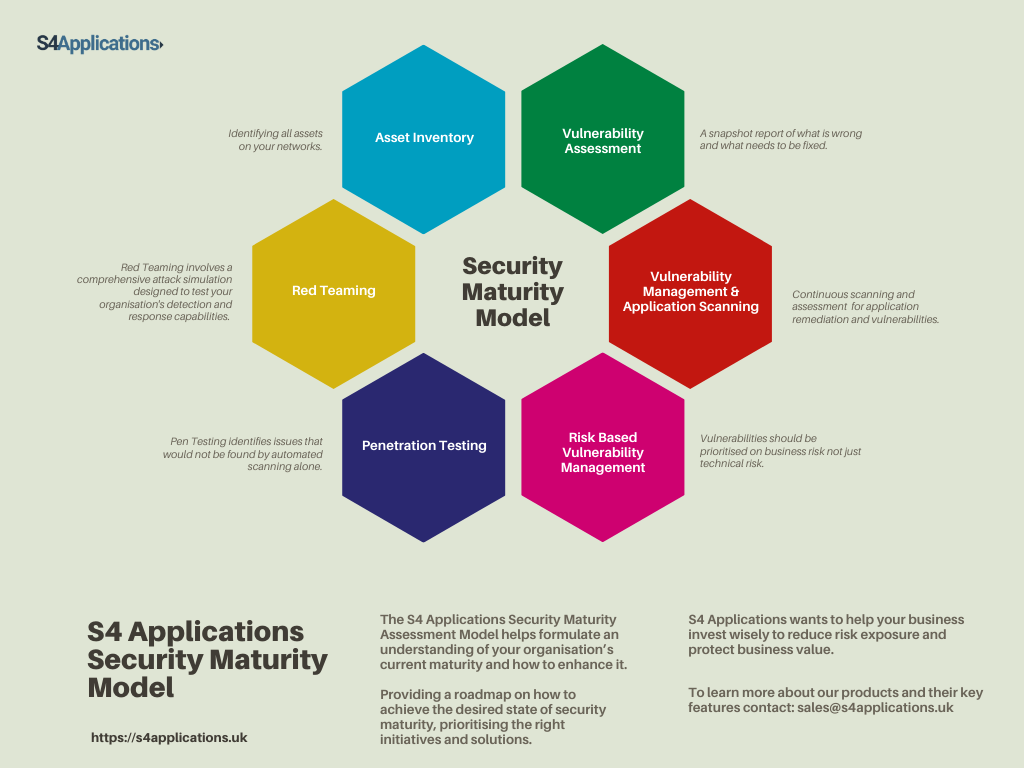
S4 Applications will help you plan a pragmatic cyber-security programme, to constantly review an organisation’s current security posture and provide a roadmap on how to achieve an appropriate level of security maturity, prioritising the right initiatives and solutions.
Where to start?
S4 Applications can help your financial services business review its ability to protect assets and respond to cyber threats. We have delivered successful solutions for insurance companies, investment houses, wealth management and banks.
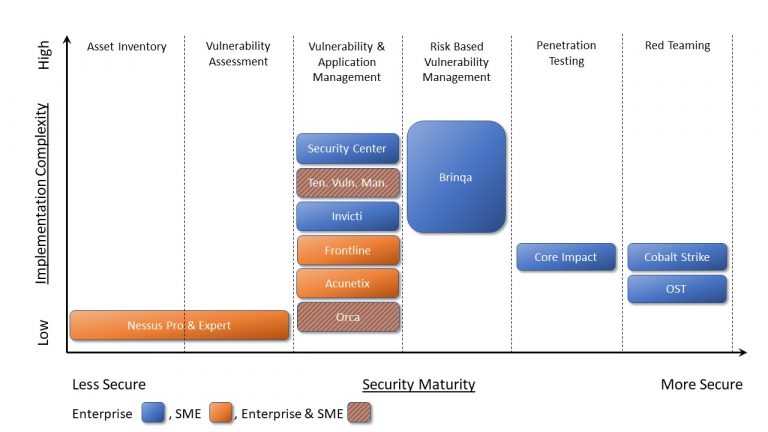
We have created our own Cyber Security Maturity Assessment Model to help your business assess your current security posture, attack surface, and existing plans and solutions. Contact us to learn more about the support that we can provide to help you assess where your security strategy stands.
Protection at the Earliest Stages
By integrating your security software within your development lifecycle, you can automatically screen for vulnerabilities in all your web applications as soon as the developers add new or modify existing code. It is far better making the effort to find a vulnerability in a pre-production system, rather than wait for it to be released.
Identifying all assets on your network that require a level of protection, you may be surprised to find there are more than you think. Businesses have a multitude of unknown assets in their environments that could compromise their security over the long run.
Similarly depending on the type of asset the level of protection required can vary. For example a smart fridge or security camera may require a different level of network protection compared to a finance server or customer database, although again all too often they are housed within the same corporate network.
Read more about: Vulnerability Management Programme and security prioritisation.
Product Recommendation
Web Security with Compliance in Mind
In a constantly changing world, you need a reliable web security solution to protect your customers and the reputation of your business.
Being able to assess, manage and measure cyber risk across the attack surface and communicate the level of this risk in business terms helps to make better strategic decisions.
As a Tenable partner, S4 Applications will work with your business to help you understand your attack surface, priorities, and goals and develop a roadmap to deploy the right solution for your needs.
Product Recommendation
Gain the Best Protection on the Market
You can scan complex websites and web applications, independent of the technologies used to create them. This allows you to protect your own web applications as well as third-party products.
By regularly scanning your environment your business can continuously identify new vulnerabilities known as CVEs, when adding software, (such as Microsoft Windows, Apache Web Server and Adobe Acrobat Reader) and hardware (such as firewalls, routers, switches and servers) to your network.
As part of your security strategy, alongside scanning for infrastructure vulnerabilities it is equally important to scan for application vulnerabilities.
In an ideal world scanning for application vulnerabilities becomes an intrinsic part of the software development lifecycle. The objective being, that no security vulnerabilities ever get into a software release version.
Product Recommendation
Case study: Fortune 500 Financial Services Firm : Vulnerability Risk
The financial services firm provided investment management services across the Americas, Europe and Asia.
As a cutting edge financial services organisation they were involved in high-value business transactions.
So, it was crucial for them to ensure that the technology infrastructure enabling critical business processes was secure and protected against compromise.
Using the Brinqa solution, the customer improved visibility into their technology infrastructure and addressed critical questions of cyber risk.
Enhance Your Vulnerability Management
A large number of assets means a lot of potential issues that need to be prioritized. Automating the process of identifying and managing vulnerabilities while guiding your team through the remediation process as soon as an issue is found.
Vulnerabilities should be prioritised on business risk not just technical risk; this is the same for infrastructure based issues or application based issues. For example, if a vulnerability is identified across multiple machines (or applications), one say on the public web site, and one in engineering, a typical, technical risk-based approach would rate them as equally dangerous, whilst a business risk approach would focus on the public web site first as this is where the highest risk really lies.
Read more about: Vulnerability Management Programme and using dashboards.
Product Recommendation
Case study: ING EURASIA IT Audit Team
An international financial institution such as ING Insurance that has offices all over the world, remote employees, and a sophisticated infrastructure, depends heavily on web applications.
Web applications such as internal portals, external portals, life insurance and investment management websites, as well as, online banking web applications are used to share data among all of the corporation’s offices and employees.
When a company has the need to audit many web applications on a continuous basis, they need to make sure that the right tools are used to detect all web application vulnerabilities possible, to keep malicious hackers out and make sure their customers’ money is secure at all times.
Product Recommendation

Next Steps
S4 Applications can help your business review its ability to protect assets and respond to cyber threats. Our Vulnerability Management Programme can help you identify the automated processes, responsibilities, priorities and integration needed to ensure nothing gets missed.
Those pillars are as follows:
- Integration of Data Sources
- Prioritisation of Security Issues
- Automation of the Process
- Visualisation and Reporting

