Cobalt Strike
Replicate the tactics and techniques of an embedded advanced adversary.
Software For Adversary Simulations & Red Teams
Threat Emulation Software
Fortra’s Cobalt Strike is a powerful threat emulation tool that provides a post-exploitation agent and covert channels ideal for Adversary Simulations and Red Team exercises, replicating the tactics and techniques of an advanced adversary in a network.
These tools complement Cobalt Strike’s solid social engineering process, its robust collaboration capability, and unique reports designed to aid blue team training.

Replicating Tactics & Techniques Of An Adversary In A Network.
Cobalt Strike’s system profiler is a web application that maps your target’s client-side attack surface, providing a list of applications and plugins it discovers through the user’s browser.
You can also deliver an attack using Cobalt Strike’s spear phishing tool using preconfigured templates or repurpose saved emails and deliver a weaponised document.
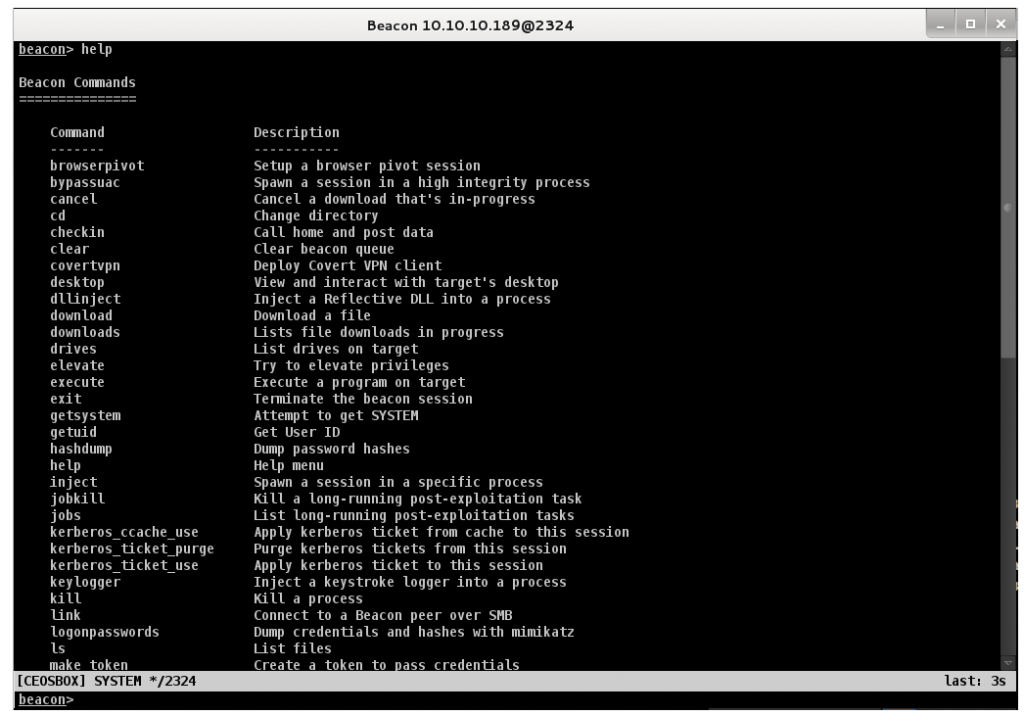
Control Your Target’s Network With Cobalt Strike’s Beacon.
Malleable C2, Beacon’s flexible Command and Control language, users can modify network indicators to blend in with normal traffic or cloak its activities by emulating different types of malware.
Beacon can perform various post-exploitation activities, including PowerShell script execution, keystroke logging, capturing screenshots, downloading files, and spawning other payloads.
This post-exploitation payload uses an asynchronous “low and slow” communication pattern that’s common with advanced threat malware. Beacon will phone home over DNS, HTTP, or HTTPS. Beacon walks through common proxy configurations and calls home to multiple hosts to resist blocking.
Prioritise Vulnerabilities.
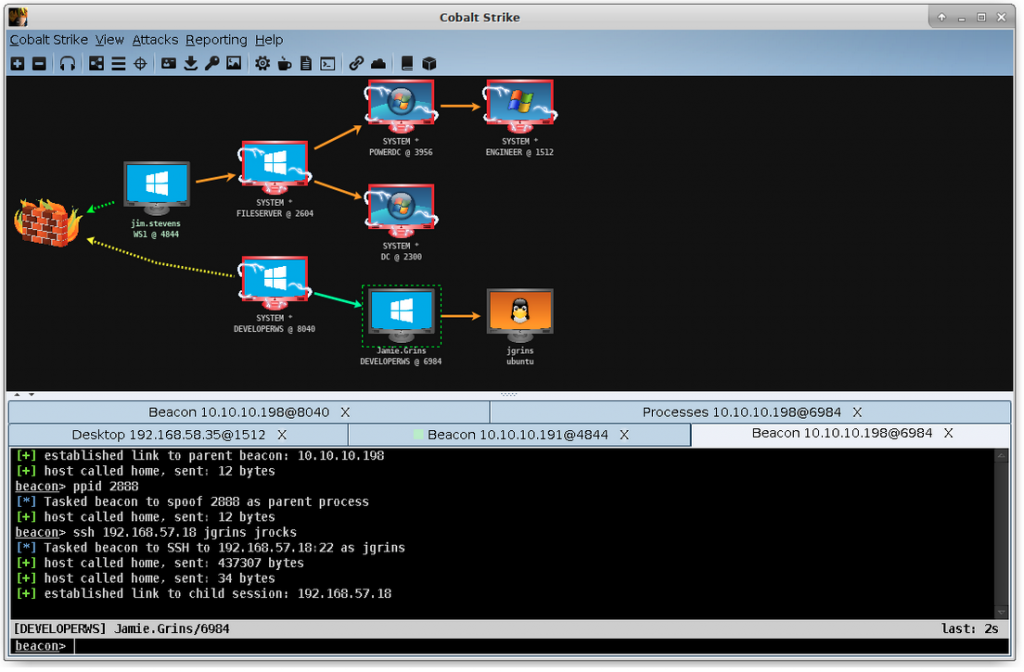
Cobalt Strike is optimised to capture trust relationships and enable lateral movement with captured credentials, password hashes, access tokens, and Kerberos tickets.
Why Cobalt Strike?
Cobalt Strike gives you a post-exploitation agent and covert channels to emulate a quiet long-term embedded actor in your customer’s network. Malleable C2 lets you change your network indicators to look like different malware each time. These tools complement Cobalt Strike’s solid social engineering process, its robust collaboration capability, and unique reports designed to aid blue team training.
Next Steps - Get Started
As a Fortra partner, S4 Applications works with clients to help them understand their attack surface, priorities, and goals. We develop a roadmap to deploy the right solution for your needs. Read more about our Fortra case studies, learn more about Fortra or contact S4 Applications to request a demo.
Related Resources
What are Cobalt Strike doing to evade EDR?
Cobalt Strike and Endpoint Detection & Response (EDR) solutions.
Ransomware Simulation by Core Impact
Core Impact’s new ransomware simulation feature is a great way to prevent malware from stealing your data or locking you out of your computer.