S4 Applications Cyber Security Maturity Assessment Model
Security is a process not a “thing”. An organisation can never be “secure” but it can be “more secure” than it was. The S4 Applications Cyber Security Maturity Assessment Model helps formulate an understanding of your organisation’s current maturity and how to enhance it.
A planned and pragmatic cyber-security programme will constantly review an organisation’s current status quo. Providing a roadmap on how to achieve the desired state of security maturity, prioritising the right initiatives and solutions.
S4 Applications wants to help your business invest wisely to reduce risk exposure and protect business value. Walk through our 6 step Maturation Model below to get to grips with what your current maturity level is.
Where to start?
S4 Applications can help your business review its ability to protect assets and respond to cyber threats. Use our Cyber Security Maturity Assessment Model to assess your current security posture, attack surface, and existing plans and solutions. In simple terms, where does your security strategy stand? What are your biggest risks? What are your regulatory and compliance obligations? Where should you focus your efforts? What are your aspirations?
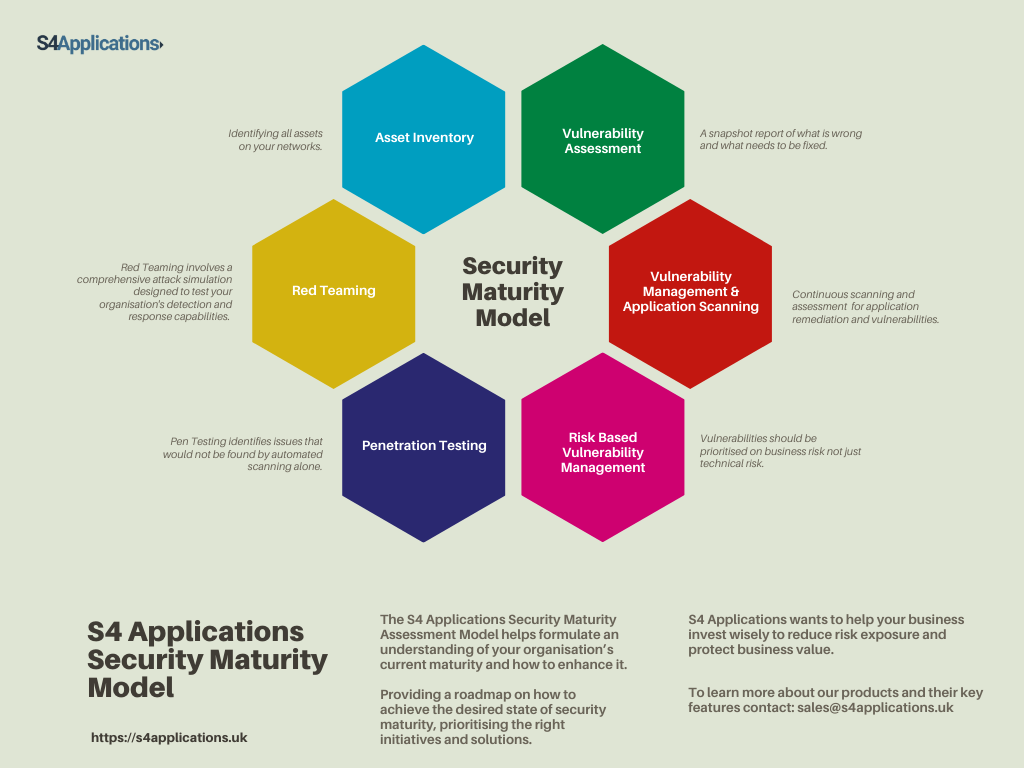
Our 6 step maturity Assessment model
Step 1 – Asset Inventory
Identifying all assets on your network that require a level of protection. You may be surprised to find there are more than you think – all too often, companies possess a multitude of unknown assets in their environments that could compromise their security over the long run.
Similarly depending on the type of asset the level of protection required can vary. For example a smart fridge or security camera require a different level of network protection to a finance server or customer database, although again all too often they are housed within the same corporate network.
An Asset Inventory provides clarity and an invaluable starting point for strengthening your security posture.
Product Recommendation
Step 2 – Vulnerability Assessment
A snapshot report of what is wrong and what needs to be fixed. As mentioned its common for businesses to have a vast pool of unknown assets and poorly configured network devices. Undertaking a vulnerability assessment uncovers these weaknesses and provides a clear view of the baseline maturity of your current security configurations.
Taking a snapshot allows us to make immediate recommendations to strengthen your security posture and help mitigate risk by using the maturity assessment model.
Product Recommendation
Based upon extensive work with enterprise customers we have compiled a list of eight best practice steps in a blog for An effective vulnerability management programme, read them as you review our Maturity Assessment Model.
Step 3a – Vulnerability Management
Continuous vulnerability assessment and remediation. By regularly scanning your environment your business can continuously identify new vulnerabilities known as CVEs, when adding software, (such as Microsoft Windows, Apache Web Server and Adobe Acrobat Reader) and hardware (such as firewalls, routers, switches and servers) to your network.
Scans can be run on any number of assets to ascertain known CVEs, as well as looking at versions of files and behaviours to understand if any part is susceptible to a given CVE and the remediation action required to close off those vulnerabilities.
Product Recommendation
There are several products that can deliver this functionality, it all depends on you, so we have built a decision tree to help you decide.
Step 3b – Application Scanning
If your company has applications that you have built yourselves or come from an external vendor, then these can have security issues. The issues could be caused by the writers of the application or by inclusion of 3rd party software that has issues. The Equifax hack and data exfiltration from 2018 was caused by the use of a vulnerable Apache Struts library.
As part of your security strategy, alongside scanning for infrastructure vulnerabilities it is equally important to scan for application vulnerabilities.
In an idea world scanning for application vulnerabilities becomes an intrinsic part of the software development lifecycle. The objective being, that no security vulnerabilities every get into a software release version.
Product Recommendation
Step 4 - Risk-Based Vulnerability Management
Vulnerabilities should be prioritised on business risk not just technical risk; this is the same for infrastructure based issues or application based issues. For example, if a vulnerability is identified across multiple machines (or application), say one on the public web site, and one in engineering, a typical, technical risk based approach would rate them as equally dangerous, whilst a business risk approach would focus on the public web site first as this is where the highest risk really lies.
Product Recommendation
Read more about the Maturity Assessment Model and how to assess your organisation’s security posture in our blog.
Step 5 – Penetration Testing
Penetration Testing identifies issues that would not be found by automated scanning alone. It is the holistic combination of skilled human and software intervention for uncovering potential vulnerabilities within your environment. A penetration tester will employ the same techniques as a potential hacker might undertake in an attempt to infiltrate your networks, install remote agents or ex-filtrate data.
The pen tester may start out from the public Internet, or with a targeted phishing campaign, or perhaps even sit in your company car-park trying to get onto the corporate Wi-Fi, or access one of your remote offices as a an external visitor would, then plug something onto the network. A successful penetration test would be defined as one in which your defences prevent such nefarious access.
Product Recommendation
Step 6 – Red Teaming
If you’re looking to protect your organisation from cyber threats, consider incorporating Red Teaming solutions. They simulate real-world attacks on your networks, systems, and applications to identify and exploit vulnerabilities in a controlled manner. By doing so, you can proactively address weaknesses in your security infrastructure before attackers have a chance to exploit them.
Red Teaming involves a comprehensive attack simulation designed to test your organisation’s detection and response capabilities. With these solutions, you can gain valuable insights into your organisation’s security posture, identify areas for improvement, and develop more effective security strategies.
Product Recommendation
Next Steps - How To Get Started
To learn more about our products and their key features talk to an expert at S4 Applications. We can work in partnership with your business and walk you through a maturity assessment model.