With ransomware attacks now becoming the norm and a huge threat to organisations, ranging from small to enterprise, I thought it worthwhile to look at the profile of a ransomware attack, and the steps you can proactively take to prevent one.
There are lots of deep dives into specific, high-profile attacks already out there, so in this blog I will keep things at a high level and focus on the actions you can take to prevent one.
The steps that an attacker will go through are in summary:
- Gain a foothold
- Escalate privilege
- Exfiltrate data if wanted
- Compromise backups / recovery plans
- Encrypt data
- Issue ransom demand and manage payment
We can dive into the details of each of these in turn below.
Some history first
Ransomware attacks first started out as completely automated affairs, and to be honest, if your home PC gets hit with one today, then it probably still is a completely automated attack. The ransoms demanded are typically a few hundred $ / € / £, and at this price, humans are not orchestrating the attack; it was a high volume, low value business for the attackers.
What the ransomware attackers noticed over time, was that they were occasionally hitting a large organisation, encrypting large amounts of data and still charging $500. They worked out that they could charge an organisation a lot more money for the same process. So, the attackers split their business model into two:
- High volume, low value business to consumer (B2C), and
- Low volume, high value business to business (B2B)
Most of this blog talks about the B2B business with the above 6 steps, but I want to quickly discuss the B2C model. The B2C model really only has a few steps as follows:
- Gain a foothold
- Encrypt data
- Issue ransom demand and manage payment
The way that an attacker gains a foothold, is the same as with the B2B ransomware attack.
The data encryption is typically just what can be found on the local PC, for which no escalation of privileges is needed, and any network drives that can be accessed are encrypted. If we personally get hit by this, it is our photos and probably a few documents (PhD thesis anyone) that drive us to pay the ransom?
The payment mechanism would also be automated so that nobody at the attacker’s end is involved to keep the effort involved at the minimum.
The way that you prevent this is to have a good data backup. In the B2B model as described below the attackers typically try to compromise the backup, but this requires a human to be involved, and for $500 they are not going to bother.
As very small percentage of people actually have a backup, this model works well for the attacker!!
A B2B attack
Firstly, I should clarify, much as we consider the attackers as criminals and extortionists, they consider themselves as “business people”. Whilst I don’t like using “B2B” as it glamourises their work, it is a short-hand term that we are all familiar with and it does explain how they work and their target market.
Getting started – gaining a foot hold
Whilst they could attack your public facing firewall and attempt entry from there, it is unlikely that this would work. They will probably use one of the following approaches to gain access to the inside of your network:
Get a user to run some of their code
To start things off, the attacker will try and get a user to run some of their malicious code. This may be in the form of a phishing attack, but these are relatively easy to spot these days. They may also be as part of a “Spear Phishing Attack” which is harder to spot.
With Spear Phishing, the attacker spends 10 minutes on LinkedIn and learns who probably works for who. The attacker then sends an email from say the CFO to someone in finance saying “Please find attached the Excel we discussed earlier”, or from head of Sales to a Sales person saying “Revised Commission Plan”.
They try and get the user to do something without thinking. Sometimes this is opening an attachment that is malicious, possibly enabling macros in Excel. The other is to click a link and open / run what is on the other end.
In an ideal world your email spam filtering will prevent this from getting to its destination. In the event that the email is delivered, you hope that your AV (anti-virus) software will prevent it from doing any damage.
With fully patched software, you should be good on both of these. I also appreciate that me writing “fully patched software” is much easier than making it happen (as I write this my PC wants to re-boot to install patch Tuesday).
Use a valid username / password
Some organisations may look like a good target to an attacker, but they just cannot get through the Spam filter. Here they may try approaching disgruntled members of staff, current or past, and ask them to help. https://www.glassdoor.com/ is a great place for them to go looking.
Companies often forget to disable user accounts of people that have left, this is a great way in. They may also use the same password on many systems and never change it; again, a great way to gain entry.
Whilst users hate it, secure, long passwords are important. Wikipedia lists the top 10,000 most common passwords; longer ones are also available. Are you really sure that none of your users have a password on this list?
Good password and user account hygiene is imperative to prevent an attack.
Escalate Privilege
To do real damage, the attacker needs to have access to a user account that has higher privilege (often referred to as Administrator, Root or System).
These privileged accounts allow them to compromise the backups, cover their tracks by editing logs and gain access to the most important files for the later steps.
Escalation of privileges is typically done using un-patched vulnerabilities.
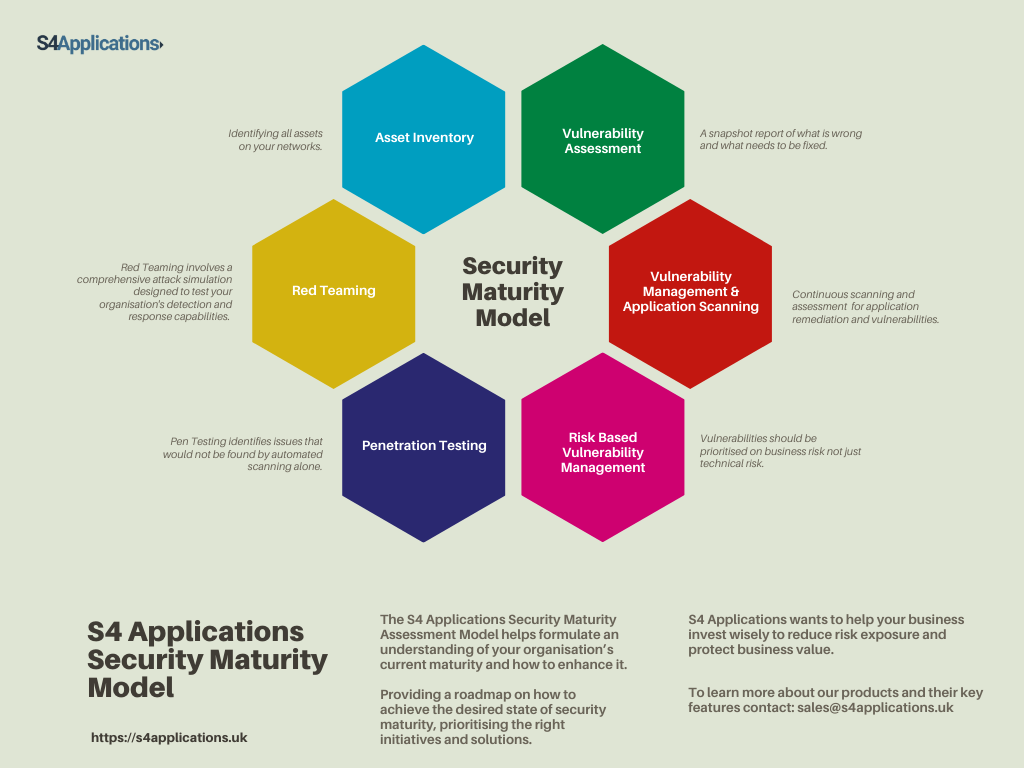
To learn more about vulnerability management, read out blog: Staying safe with Risk Based Vulnerability Management.
Exfiltrate Data if wanted
In the earlier attacks, attackers would just encrypt the data and ask for the ransom. This was fine for home PCs, but organisations typically have backups. This meant that the victim could just restore the backup, not pay the ransom, and move on; inconvenient but the victim could get through it.
To ramp-up additional pressure for victims to pay the ransom, attackers copy all the confidential data, and then threaten to release ever more documents to embarrass the organisation into paying.
Typically ransomware criminals now offer their victims 2 prices options:
- Data decryption and a promise by the attacker to delete their copy of the data
- No data decryption (victim restores backups) and a promise by the attacker to delete their copy of the data
Interestingly there is a big incentive for the attackers to build a strong, positive reputation. They need to be trusted to provide the required decryption tools and to delete their copies of the data. If word gets out that attacker X didn’t decrypt the data properly, or that they released sensitive documents even after payment, then their reputations would be destroyed, and nobody would pay the ransom.
There are even [unconfirmed] stories of some ransomware criminals refunding ransoms where the decryption didn’t work, in an attempt to keep a positive reputation.
Compromise Backups
Organisations keep backups, and these are a great strategy for combatting ransomware. The attackers know this, so will do their best to compromise them in some way or another.
Encrypt Data
This is the “relatively” easy part. The attacker will start the encryption on say a Friday night so that it has as long as possible to run before being spotted.
They will try and have the encryption running on as many machines as possible, at once, to get the best performance, and complete the job in the shortest time possible.
Interestingly, their decryption tools often don’t run as fast!!
Issue Ransom Demand
This is the really easy bit; they will ask for a number of Bitcoins (or other crypto currency) to be paid to a given account so that you can receive the decryption tools, and delete copied data.
Often, they will ask for a higher ransom in Bitcoin than in other currencies, because Bitcoin is not 100% anonymous and increases their risk.
Read our blog: How crypto-currencies professionalised hacking.
What you can do
The main focus should be on preventing step 1 “Gain a foothold” because once the attackers are inside your network, it is almost too late.
There are 3 main areas to look at:
Vulnerability Scanning
As discussed above, the attack doesn’t come in through the front door where your firewall is, they come in through emails that persuade users to do things that they shouldn’t. This means that your users need to be trained, their emails scanned and their machines as up-to-date as possible.
Many of the things that attackers will use, are based upon software vulnerabilities within users Workstations. The vendors (Microsoft, Adobe, Apple and so on) issue patches regularly to fix known issues, so all users should be running the latest of everything.
A vulnerability scanner (we offer 2, Tenable and Fortra VM ) will help identify machines that are not current, and are therefore a danger.
You will also find that this is one of the first steps on our Maturity Assessment Model.
Email Scanning
There is a very large market out there for email scanning tools. We have never tested this type of tool in the lab (like we have with vulnerability scanners) so don’t feel happy to recommend any specific tool, we will leave that to Gartner and so on.
Anecdotally, we use Microsoft’s Office 365 and it seems to do a good job for us.
Manage User’s identities
This is a very large area (Identity Access Management) that again we don’t specialise in it, so cannot make any recommendation. Remember users have access to not just domain resource but also things like the CRM, the finance system and so on, they can all be used as part of campaigns. Some of these systems may be SaaS solutions and outside of your direct control.
Think if you have a cloud CRM, someone has a weak password there and an attacker gets access to it. That attacker goes into this account, up-loads a malicious Excel file to a sales opportunity record called “Bribes Paid”. The attacker then sits back and waits for someone to open it.
Next steps
In order to remain one step ahead of these cyber-attackers, it’s important to audit your security posture regularly, especially if you have seen a surge in attacks in your industry.
Better that you know your weak spots before a hacker does. If you want help to understand how to address your vulnerabilities book a free consultation.

