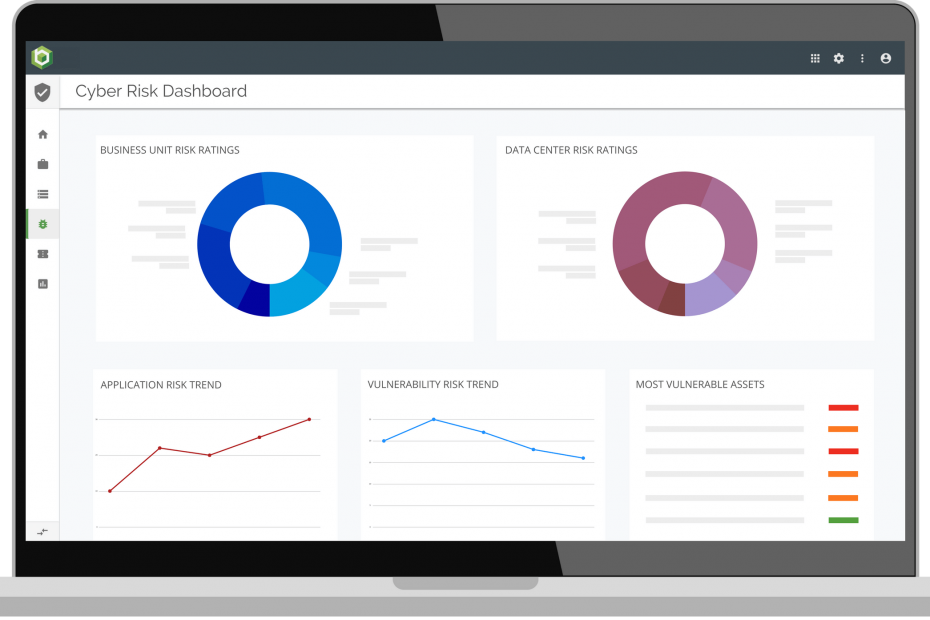
Whilst most companies seek to run a risk-based vulnerability management programme, it is very hard to implement one from scratch. Most companies do this using the following 3 steps, by gradually phasing in extra sophistication as they progress on their security journey:
- 1. Vulnerability Assessments
- 2. Vulnerability Management
- 3. Risk based vulnerability management
See our explanation of the three steps below:
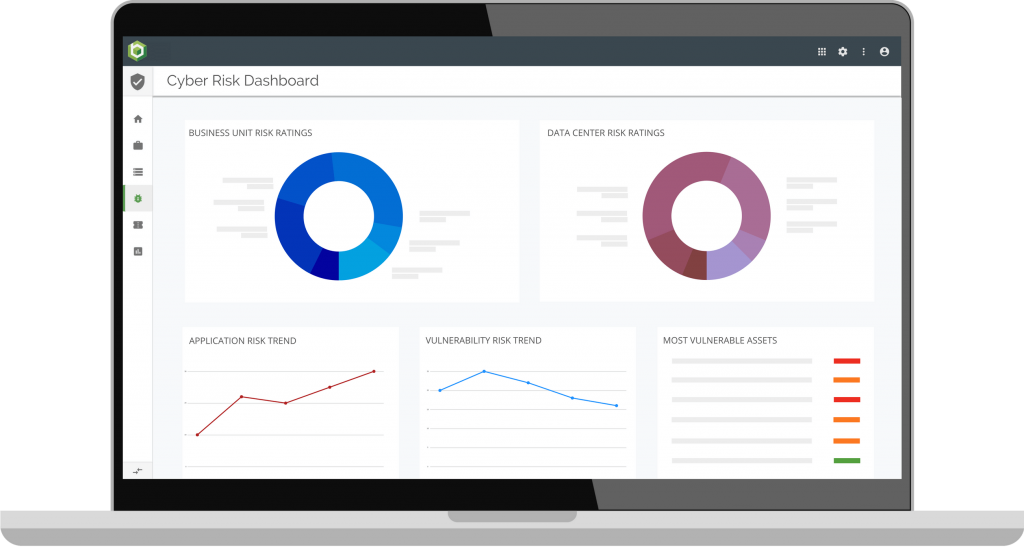
S4 Applications explanation of the 3 steps:
1. Vulnerability Assessment:
The act of scanning for potential vulnerabilities (security issues) in software such as Microsoft Windows, Apache Web Server and Adobe Acrobat Reader, or in hardware such as firewalls, routers, switches and servers, that produces a list of potential issues.
Continuous vulnerability scanning is the first step to truly understanding where your organisation’s vulnerabilities are, ensuring your business can then work to eliminate the more serious vulnerabilities affecting your valuable resources.
2. Vulnerability management:
A comprehensive Vulnerability Assessment programme. Running cyclical vulnerability assessments to identify threats then taking the output data to classify and prioritise risks based on severity (known as CVSS score) for remediation and mitigation.
3. Risk based vulnerability management:
The final step in increasing vulnerability maturity. Vulnerabilities are prioritised based on business risk, rather than just technical risk.
For example, if a vulnerability is identified across multiple machines, say one on the public web site, and one in engineering, a typical Vulnerability Management approach would rate them as equally dangerous, whilst a risk-based approach would focus on the public web site first as this is where the highest business risk lies.
Read more about Staying safe with Risk Based Vulnerability Management in our blog.
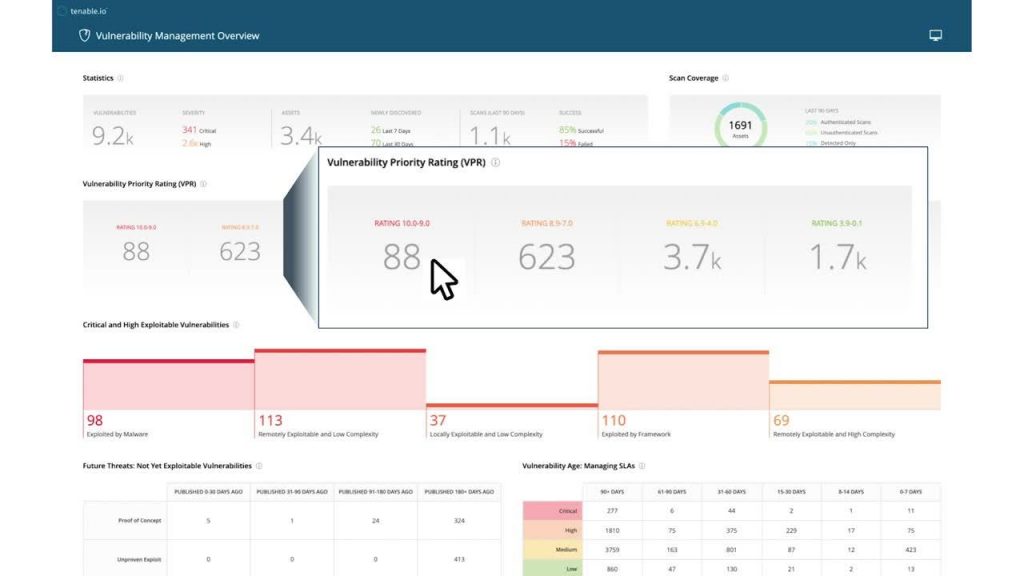
Focusing on business
Depending on your level of vulnerability maturity, S4 Applications has a range of solutions that can help prevent unauthorised attacks and protect business continuity and reputation.
From Brinqa, Invicti and Tenable, they can all help prevent unauthorised attacks and protect business continuity and reputation.
If you want to learn more about security maturity read: Assess your security Posture with our Security Maturity Model.