In today’s interconnected digital landscape, cybersecurity threats are constantly evolving, making it imperative for organisations to stay vigilant in protecting their sensitive data and assets. One crucial aspect of a robust cybersecurity strategy is conducting regular vulnerability assessments. These assessments serve as a proactive measure to identify and mitigate potential security weaknesses before they can be exploited by malicious actors.
Over 560,000 new cyber threats are found a day and 81% of all UK Businesses who suffer from a Cyber Security Attack are Small to Medium Sized Businesses (SMBs/SMEs) (Source)
Whether you’re a cybersecurity professional seeking to bolster your organisation’s defences or a business owner aiming to safeguard your digital assets, understanding the fundamentals of vulnerability assessments is key to maintaining a strong security posture in today’s threat landscape.
At S4 Applications it’s our aim to stay on top of vulnerabilities and keep your business protected, if you are unsure what you need please get in touch here.
What is a vulnerability assessment? Definition
A vulnerability assessment is a systematic process of identifying, analysing, and prioritising security vulnerabilities in systems, networks, applications, or other IT assets. The primary goal of a vulnerability assessment is to uncover weaknesses that could potentially be exploited by attackers to compromise the confidentiality, integrity, or availability of an organisation’s data and resources. By conducting vulnerability assessments, organisations can proactively identify and address security risks, thereby enhancing their overall cybersecurity posture and reducing the likelihood of successful cyberattacks.

FREE 10 Steps to Strengthen Enterprise Security Today
What’s the difference between vulnerability assessment and penetration testing?
Vulnerability assessments primarily aim to identify potential security weaknesses within an organisation’s IT infrastructure, often using automated scanning tools. They provide a comprehensive overview of security posture by pinpointing vulnerabilities like missing patches and misconfigurations. However, they typically don’t involve exploiting these vulnerabilities.
In contrast, penetration testing, also known as ethical hacking, takes a more hands-on approach. It simulates real-world cyberattacks to actively exploit vulnerabilities and assess their impact on security. Penetration testing provides valuable insights into security controls’ effectiveness but is more resource-intensive and less frequent than vulnerability assessments.
We have a great blog post on vulnerability scanning vs penetration testing that you can read here.

In summary, while vulnerability assessments identify weaknesses without exploiting them, penetration testing actively exploits vulnerabilities to assess security posture and control effectiveness. Both are crucial for a robust cybersecurity strategy.
Why Are Vulnerability Assessments Important?
Cybercrime affects people and businesses all around the world. In the UK 32% of businesses reported suffering from a cyber attack in 2023. For medium businesses, this rises to 59%. 69% of large businesses reported an attack. It’s estimated that businesses lost up to £736 million to cyber crime in 2021. The average cost of a security brach for a medium size business is £4960 as of December 2023. You can find more info and stats on this subject on AAG.
Having your businesses attacked online is very costly and time consuming. They damage trust in your users and can have a severe impact on a business. Cyber crimes are constantly evolving which is why doing regular vulnerabilty assessments are important in maintaining robust cybersecurity defenses. These assessments are essential for several reasons:
- Early Detection of Weaknesses: Vulnerability assessments enable organizations to identify potential security weaknesses in their IT infrastructure before they can be exploited by malicious actors. By proactively uncovering vulnerabilities such as missing patches, misconfigurations, and insecure network settings, organizations can take steps to address these issues before they are exploited.
- Risk Mitigation: By identifying and prioritising vulnerabilities based on their severity and potential impact, vulnerability assessments help organisations prioritise remediation efforts effectively. This allows them to allocate resources more efficiently and address the most critical security risks first, thereby reducing the overall risk of a successful cyberattack.
- Compliance Requirements: Many regulatory frameworks and industry standards require organizations to conduct regular vulnerability assessments as part of their compliance obligations. By performing these assessments, organisations can demonstrate their commitment to maintaining a secure environment and complying with relevant regulations such as GDPR, HIPAA, PCI DSS, and others.
- Protection of Sensitive Data: Vulnerability assessments help protect sensitive data from unauthorised access, disclosure, or modification by identifying and addressing security vulnerabilities that could potentially compromise data confidentiality, integrity, or availability. By safeguarding sensitive data, organisations can preserve customer trust, avoid costly data breaches, and mitigate reputational damage.
- Continuous Improvement: Vulnerability assessments are not one-time events but rather an ongoing process. By conducting regular assessments, organisations can continuously monitor their security posture, track changes over time, and identify emerging threats and vulnerabilities. This allows them to adapt their security strategies accordingly and stay ahead of evolving cyber threats.
Types of Vulnerability Assessments
Vulnerability assessments are essential for identifying and prioritising security weaknesses within an organisation’s IT infrastructure. Depending on the scope and objectives of the assessment, there are several types of vulnerability assessments that organisations can utilise:
- Network Vulnerability Assessments: Network vulnerability assessments focus on identifying vulnerabilities within an organization’s network infrastructure, including routers, switches, firewalls, and other network devices. These assessments typically involve scanning network devices for known vulnerabilities, misconfigurations, and potential security weaknesses that could be exploited by attackers to gain unauthorised access to the network.
- Application Vulnerability Assessments: Application vulnerability assessments are targeted at identifying security vulnerabilities within software applications, web applications, and mobile applications. These assessments involve analysing the code, configuration, and behavior of applications to uncover vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms. Application vulnerability assessments are essential for ensuring the security of customer-facing applications and protecting against potential exploitation by malicious actors.
- Host-Based Vulnerability Assessments: Host-based vulnerability assessments focus on identifying vulnerabilities within individual systems or hosts, such as servers, workstations, and mobile devices. These assessments typically involve scanning the operating system, installed software, and system configurations for known vulnerabilities, missing patches, and insecure settings. Host-based vulnerability assessments help organisations identify and remediate vulnerabilities that could be exploited to compromise the integrity or confidentiality of data stored on individual systems.
- Wireless Network Vulnerability Assessments: Wireless network vulnerability assessments are targeted at identifying security vulnerabilities within an organisation’s wireless network infrastructure, including Wi-Fi routers, access points, and wireless clients. These assessments involve scanning wireless networks for known vulnerabilities, weak encryption protocols, and unauthorised access points. Wireless network vulnerability assessments help organisations identify and address security risks associated with wireless communication, such as unauthorised access and data interception.
- Cloud-Based Vulnerability Assessments: With the increasing adoption of cloud services and infrastructure, cloud-based vulnerability assessments have become essential for identifying security vulnerabilities within cloud environments. These assessments involve scanning cloud infrastructure, services, and configurations for known vulnerabilities, misconfigurations, and security weaknesses. Cloud-based vulnerability assessments help organisations ensure the security of their cloud deployments and protect against potential threats and vulnerabilities in the cloud.
By conducting various types of vulnerability assessments tailored to their specific needs and environments, organisations can effectively identify, prioritise, and remediate security vulnerabilities, thereby enhancing their overall cybersecurity posture and reducing the risk of cyberattacks.
S4 Applications Cyber Security Maturity Assessment Model
At S4 Applications we help businesses formulate a a proper cyber security model with the S4 Applications Cyber Security Maturity Assessment Model. A business can never be 100% safe but it can always be “more safe”. Our model will help provide a roadmap on how to achieve the desired state of security maturity, prioritising the right initiatives and solutions.
S4 Applications wants to help your business invest wisely to reduce risk exposure and protect business value. Let’s go through our 6 step Maturation Model below to get to grips with what your current maturity level is.
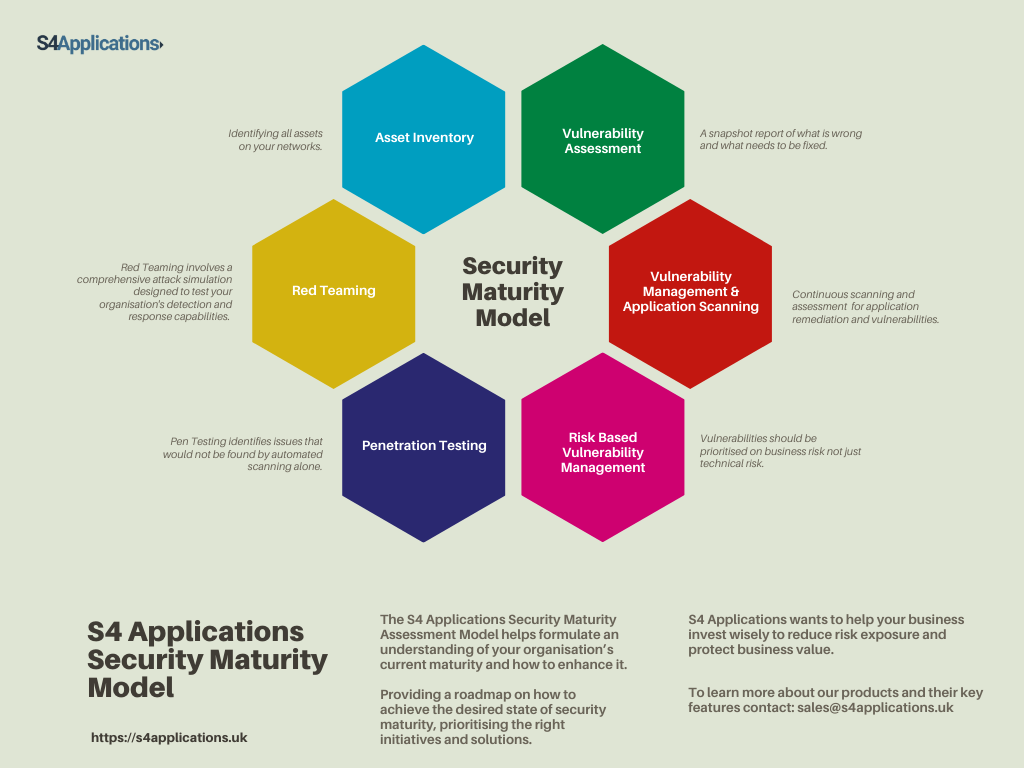
The S4 Applications Cyber Security Maturity Assessment Model is used to assess your current security posture, attack surface, and existing plans and solutions. In simple terms, where does your security strategy stand? What are your biggest risks? What are your regulatory and compliance obligations? Where should you focus your efforts? What are your aspirations?
Step 1 – Asset Inventory
Identifying all assets on your network that require a level of protection. You may be surprised to find there are more than you think – all too often, companies possess a multitude of unknown assets in their environments that could compromise their security over the long run.
Product Recommendation
Step 2 – Vulnerability Assessment
A snapshot report of what is wrong and what needs to be fixed. As mentioned its common for businesses to have a vast pool of unknown assets and poorly configured network devices. Undertaking a vulnerability assessment uncovers these weaknesses and provides a clear view of the baseline maturity of your current security configurations.
Product Recommendation
Step 3a – Vulnerability Management
Continuous vulnerability assessment and remediation. By regularly scanning your environment your business can continuously identify new vulnerabilities known as CVEs, when adding software, (such as Microsoft Windows, Apache Web Server and Adobe Acrobat Reader) and hardware (such as firewalls, routers, switches and servers) to your network.
Product Recommendation
There are several products that can deliver this functionality, it all depends on you, so we have built a decision tree to help you decide.
Step 3b – Application Scanning
If your company has applications that you have built yourselves or come from an external vendor, then these can have security issues. The issues could be caused by the writers of the application or by inclusion of 3rd party software that has issues. The Equifax hack and data exfiltration from 2018 was caused by the use of a vulnerable Apache Struts library.
Product Recommendation
Step 4 – Risk-Based Vulnerability Management
Vulnerabilities should be prioritised on business risk not just technical risk; this is the same for infrastructure based issues or application based issues. For example, if a vulnerability is identified across multiple machines (or application), say one on the public web site, and one in engineering, a typical, technical risk based approach would rate them as equally dangerous, whilst a business risk approach would focus on the public web site first as this is where the highest risk really lies.
Product Recommendation
Step 5 – Penetration Testing
Penetration Testing identifies issues that would not be found by automated scanning alone. It is the holistic combination of skilled human and software intervention for uncovering potential vulnerabilities within your environment. A penetration tester will employ the same techniques as a potential hacker might undertake in an attempt to infiltrate your networks, install remote agents or ex-filtrate data.
Product Recommendation
Step 6 – Red Teaming
If you’re looking to protect your organisation from cyber threats, consider incorporating Red Teaming solutions. They simulate real-world attacks on your networks, systems, and applications to identify and exploit vulnerabilities in a controlled manner. By doing so, you can proactively address weaknesses in your security infrastructure before attackers have a chance to exploit them.
Product Recommendation
Enterprise: Outflank Security Tooling (OST)
Cyber Security Vulnerability Assessment
In conclusion, vulnerability assessments are indispensable tools in the arsenal of cybersecurity professionals, enabling organisations to proactively identify and mitigate potential security weaknesses before they can be exploited by malicious actors. Through the systematic identification, analysis, and prioritisation of vulnerabilities in systems, networks, applications, and other IT assets, vulnerability assessments provide organisations with valuable insights into their security posture and help them make informed decisions to safeguard their digital assets.
By understanding the fundamentals of vulnerability assessments and following best practices for conducting them effectively, organizations can strengthen their cybersecurity defenses and reduce the risk of cyberattacks. From defining the scope and objectives of the assessment to conducting thorough vulnerability scanning, analysing findings, and developing remediation plans, each step in the vulnerability assessment process plays a crucial role in enhancing security posture and protecting against potential threats.
In today’s constantly evolving threat landscape, where cyber threats are becoming increasingly sophisticated and pervasive, the importance of vulnerability assessments cannot be overstated. By integrating vulnerability assessments into their cybersecurity strategy and making them an ongoing practice, organisations can stay ahead of emerging threats, comply with regulatory requirements, and demonstrate their commitment to maintaining a secure environment for their stakeholders.
In essence, vulnerability assessments empower organisations to take proactive measures to identify, prioritise, and remediate security vulnerabilities, thereby strengthening their overall cybersecurity posture and reducing the risk of data breaches, financial losses, and repetitional damage. By embracing vulnerability assessments as a fundamental component of their cybersecurity strategy, organisations can better protect their digital assets and mitigate the impact of cyber threats in an increasingly interconnected world.
Get in touch with S4 Applications today to get on top of your security today.
