With new cyber threats appearing everyday which are evolving rapidly, businesses need robust solutions to safeguard their data, systems, and reputation.
This is where Tenable comes into play. As a leading provider of cybersecurity solutions, Tenable offers a suite of products and services designed to help organisations identify, prioritise, and mitigate cybersecurity risks effectively.
In this blog post, we’ll delve into the world of Tenable, exploring its comprehensive range of products and solutions, its approach to vulnerability management and risk assessment, and its impact on the cybersecurity landscape. Whether you’re a small business looking to enhance your cybersecurity defences or a large enterprise seeking to stay ahead of emerging threats, Tenable offers the tools and expertise you need to succeed in today’s dynamic threat landscape.
Interested in learning more about how Tenable can help secure your organisation? Contact S4 Applications today for a free consultation and discover how Tenable’s solutions can elevate your cybersecurity strategy to the next level.

What is Tenable and how can S4 Applications help?
Tenable have a range of products that S4 Applications supply which help with various security risks in your business. One of the key points in Tenable is that it translates vulnerability data into real business insights.
Vulnerability management is an integral part of maintaining your organisation’s computer and network security, scanning your IT infrastructure or software applications to locate and address known software vulnerabilities.
Tenable’s approach to exposure management combines visibility across the attack surface with business context. Tenable Nessus is one of the most widely-deployed security technologies in the world and the go-to product for virtually every security professional.
Tenable knows that there is no one-size-fits-all approach to cyber security. The Tenable platform can comprehensively evaluate, manage, and measure cyber risk across the modern attack landscape, translating cyber risk into business terms to support more informed strategic decisions.
Tenable Security Center on-premise solution
Enterprise and SMB organisations – Tenable Security Center (formerly Tenable.sc) powered by Nessus, is Tenable’s on-premise solution for vulnerability management. Ensuring continuous discovery and assessment of your network by monitoring unexpected network changes before they turn into breaches.
Tenable Vulnerability Management SaaS solution
Enterprise and SMB organisations – Tenable Vulnerability Management (formerly Tenable.io) provides the data you need to identify, investigate, and prioritise the remediation of vulnerabilities as a cloud-delivered solution.
Fortra Vulnerability Manager is also a SaaS vulnerability management solution suitable for SMBs and MSPs.
Tenable Nessus Professional
Consultants, Pen Testers and Security Practitioners – Nessus Professional is the industry standard vulnerability scanner.
With pre-built templates to help understand where your vulnerabilities are and what to do about them, “snooze” select issues to have them disappear from view until you’re ready to address them. Click here to learn more about the product.
Tenable Nessus Expert
Consultants, Pen Testers, Developers and SMB’s – Nessus Expert, built for the modern attack surface, enables you to see more and protect your organisation from vulnerabilities.
A fully portable vulnerability assessment, Nessus Expert expands upon Nessus Professional to understand risk beyond traditional IT assets. Click here to learn more about the product.
Cloud Cyber Security
As businesses increasingly rely on cloud services for their data, applications, and operations, securing these environments becomes crucial. This involves implementing measures such as encryption, access controls, and robust threat detection and response systems. The aim is to ensure that cloud resources remain confidential, intact, and accessible while defending against cyber attacks, data breaches, and other security risks. By prioritising cloud cyber security, organisations can safely leverage the benefits of the cloud without compromising their sensitive information.
If your businesses use cloud technology to store data, then it’s worth getting in touch with us today to make your cyber security a priority.
Tenable and Cloud Cyber Security
Tenable has a product that is specifically made for Cloud Security. They help a business find vulnerabilities in their cloud systems, by finding misconfigurations, vulnerabilities and excessive permissions with our Cloud-Native Application Protection Platform (CNAPP).
Tenable Cloud Security offers CWP, CSPM, CIEM, CDR, KSPM, IaC, JIT and CNAPP. What are each of these?
What is Agentless Workload Scanning (CWP)?
When you have various digital “jobs” running , like virtual machines (VMs), serverless functions, it’s important to make sure all these jobs are safe and not vulnerable to cyber attacks. Tenable helps by thoroughly checking these jobs for any weaknesses. This includes looking for hidden data (like passwords), sensitive information (like personal data), harmful software (malware), and incorrect settings that could lead to problems.
By using a leading vulnerability management tool, you can efficiently scan all these different digital jobs to find and fix these issues, keeping your online activities secure and running smoothly.
What is Compliance and Reporting (CSPM)?
Your cloud systems have lots of different settings and configurations. These setups need to be safe and follow certain rules and standards to protect your information.
Continuously reviewing these settings means regularly checking to make sure everything is set up correctly and securely. This helps in staying compliant with important regulations and standards like CIS, HIPAA, NIST, PCI-DSS, GDPR, and others. These are like guidelines to keep your data safe and private.
What is Cloud Infrastructure and Entitlements Management (CIEM) Security?
Various people and automated systems (machines) need access to your online resources, like data and applications. It’s crucial to manage who can access what to keep everything secure.
Securing all identities by making sure both people and machines have the right permissions to access only what they need. This involves using top-notch entitlements management, which is a way to control and assign these permissions.
Detecting risky permissions and toxic mixes by identifying any access rights that could potentially lead to security issues if misused. Enforcing least privilege means giving people and machines the minimum level of access necessary to do their jobs, nothing more.
What is Threat Detection and Response (CDR)?
Threat detection and response (CDR) is like having a digital security guard watching over your online activities. Instead of just looking for known threats, this guard uses continuous behavioral analysis and anomaly detection to spot anything out of the ordinary. It’s like having a smart system that learns what normal behavior looks like and raises an alarm if something seems off.
This system works by following built-in rules and custom policies that you set up. For example, it might flag unusual login patterns or unexpected data transfers.
If something suspicious is detected, you can investigate it using activity logs. These logs keep track of everything that happens in your digital space, kind of like a diary of online activities. With easy-to-use query tools, you can search through these logs to understand what happened and take action if needed.
By automating threat detection and using detailed activity logs, you can stay one step ahead of potential security threats and keep your digital space safe.
What is Kubernetes Security (KSPM)?
Now, keeping your Kubernetes system secure is really important. But with so many moving parts, it can be hard to spot security issues and make sure everything follow the rules.
This process helps by first uncovering any security gaps – like unlocked doors or weak spots – in your Kubernetes setup. Then, it figures out which ones are the most urgent to fix. Once identified, it helps you automatically make things right to meet security standards.
It also brings all this information together in one place, so everyone involved can see what’s going on and understand how to make things better. It’s like having a clear map of your digital world, with directions on how to stay safe and secure.
What is Infrastructure as Code Security (IaC)?
When you’re building something online, instead of just checking for problems after it’s built, this process starts looking for flaws right from the beginning – like spotting cracks in the blueprint before you start building.
So, as you’re creating the blueprint for your infrastructure, it’s scanning and finding any potential weaknesses. Then, it helps you fix them right away, before they become big issues.
Once it finds and sorts out the most important problems, it lets everyone know what’s going on. This way, everyone on the team can stay updated and work together to keep things safe and strong.
How can Tenable help your business with cybersecurity?
Maintaining robust cybersecurity within your organisation necessitates effective vulnerability management. This involves the continuous scanning of your IT infrastructure and software applications to pinpoint and promptly address any known vulnerabilities, ensuring the integrity and security of your computer and network systems.
Tenable’s strategy for managing exposure integrates comprehensive visibility across the attack surface with contextual understanding of business operations. Tenable Nessus stands out as one of the most extensively adopted security technologies globally, serving as the preferred choice for nearly every security professional.
Tenable has a range of products that are designed by professionals to protect you from threats.
Tenable Nessus Professional: Tenable Nessus Professional is a powerful vulnerability assessment tool designed to help organisations identify and address security vulnerabilities within their IT infrastructure.
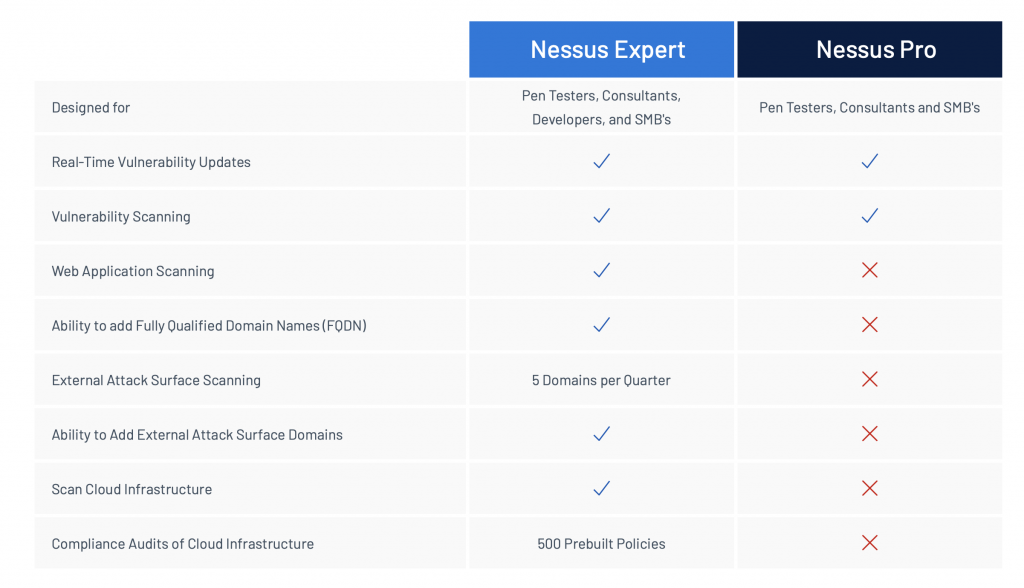
Tenable Nessus Expert: A similar product to Nessus Pro but it has more features, including: External attack surface scanning, Compliance audits of cloud infrastructure and Infrastructure as code (IAC) – Terrascan.
You can read more about the differences between Nessus Pro and Nessus Expert in this post.
Tenable Nessus Professional
Tenable Nessus Professional is a powerful vulnerability assessment tool designed to help organisations identify and address security vulnerabilities within their IT infrastructure. It offers comprehensive scanning capabilities that enable users to assess networks, systems, applications, and devices for potential security weaknesses.
Nessus Professional provides users with detailed reports that highlight vulnerabilities, misconfigurations, and potential security threats, allowing organisations to prioritise and remediate issues efficiently. It also supports compliance auditing, helping organisations adhere to industry regulations and security best practices.
Nessus Pro is generally regarded as the industry’s best vulnerability scanner.
Key features of Nessus Professional include:
- Scalability: It can scan large and complex networks with ease, making it suitable for organizations of all sizes.
- Accuracy: Nessus leverages a vast vulnerability database and advanced detection techniques to provide accurate and reliable results.
- Customization: Users can customise scans based on their specific requirements, such as targeting specific assets, IP ranges, or vulnerability types.
- Integration: Nessus seamlessly integrates with other security tools and platforms, allowing for streamlined workflows and enhanced visibility into security posture.
- Continuous Monitoring: With scheduled scans and real-time monitoring capabilities, Nessus helps organizations maintain ongoing visibility into their security posture and proactively address emerging threats.
Overall, Tenable Nessus Professional is a versatile and robust tool that empowers organisations to proactively manage their cybersecurity risk and protect their digital assets effectively.
Nesses Professional Key Features
Nessus is purposefully engineered with a deep understanding of security practitioners’ needs. Every feature is meticulously designed to simplify vulnerability assessment, making it straightforward, efficient, and intuitive. The result is a significant reduction in time and effort required to identify, prioritise, and remediate security issues.
Deploy on an device
Streamlined Effectiveness
Scan Web Applications
Your Internet-Facing Visibility
Easy to Use
Cost Effective
Accurate Visibility
Who should use Nessus Professional?
Nessus stands as the leading vulnerability scanning solution globally. It has lots of use-cases, let’s look at some scenarios where it can be used:
Nessus Pro for Penetration Testing
A penetration tester, also known as an ethical hacker, is a cybersecurity professional responsible for assessing the security of computer systems, networks, and applications by simulating cyber attacks.
Nessus Pro can be used for Penetration Testing by using Nessus to conduct comprehensive vulnerability scans before breach simulations begin, this allows pen testers to identify the areas in need of closest examination. Scans can be carried out using prefigured policies or configured to meet custom needs.
Additionally, the Live Results feature will run an assessment with every plugin update, and can further inform a pen tester’s strategy as new vulnerabilities are announced. Scan findings can quickly be turned into exported reports for IT and other stakeholders to examine, so that they’re always aware of the organisation’s level of risk.
Nessus is also fully portable, which allows the pen tester to easily move from locations or testing sites with relative ease. – You can read more about his from their full case study here.
Cybersecurity Consultants
Cybersecurity consultants use Nessus to look at a clients network to find vulnerabilities. They create reports that summarise the security of a system and create recommendations.
Nessus Pro is the number one vulnerability assessment tool so it’s able to develop plugins that address the newest vulnerabilities and threats. It’s often use a supplementary tool for pen testers. Each client a cybersecurity consultant faces will be different so the ability to customise scans, a Nessus license is transferable to different clients so it’s an easy to swap system if a consultant has lots of different clients.
Conclusion: Tenable and S4 Applications
In summary, Tenable specialises in providing comprehensive cybersecurity solutions for businesses, offering a wide range of services such as vulnerability management, cloud security, and threat detection. By utilising innovative technologies and best practices, Tenable helps organisations identify, prioritise, and remediate security risks across their digital landscapes, ensuring robust protection against cyber threats. For those interested in learning more or seeing a demonstration of Tenable’s offerings in action, reaching out to S4 Applications would be a great next step. S4 Applications can provide further information and arrange personalised demos to showcase how Tenable’s solutions can benefit specific business needs.
