Fortra
Offensive Security
Gain threat detection solutions, monitoring malicious activity.
Find your Organisation's Weak Points.
Fortra’s cybersecurity and automation offerings give your organisation the tools you need to meet the challenges of today’s threat landscape.
Having a vulnerability management programme is a critical part of maintaining compliance and reducing the risk of both internal and external attacks.
Vulnerability scans and reports pinpoint which vulnerabilities are present. Penetration tests add additional context by actually exploiting these discovered vulnerabilities.
Fortra’s vulnerability management solutions help locate, analyse, prioritise, and track security weaknesses so you know what needs to be protected.
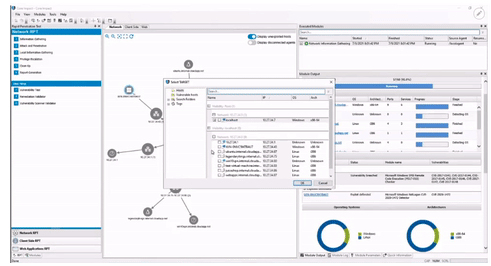
Core Impact
Core Impact is targeted at pen-testers and is an exploitation framework. This competes in a similar product category to Metasploit.
It is a workbench with a reporting engine, complete audit trail and exploits that massively speed up the work of a pen-tester. It includes network level exploits, phishing attacks and web application exploits, plus other tools like ransomware simulation.
Integrations with other Fortra solutions
Core Impact and Cobalt Strike are two powerful tools that help organizations assess the security of their environments. This PDF provides an overview of the key functionalities of each of these tools, their similarities, and how they can be used together to amplify your pen testing efforts.
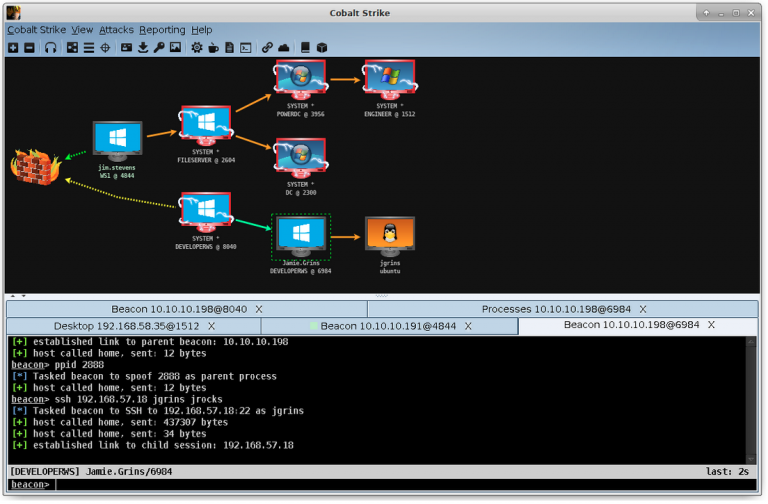
Cobalt Strike
Cobalt Strike is the industry-leading Command and Control (c2) infrastructure. This is used by most red teams (plus most malware) because of its power and EDR evasion technology.
Why Cobalt Strike?
Cobalt Strike gives you a post-exploitation agent and covert channels to emulate a quiet long-term embedded actor in your customer’s network. Malleable C2 lets you change your network indicators to look like different malware each time. These tools complement Cobalt Strike’s solid social engineering process, its robust collaboration capability, and unique reports designed to aid blue team training.
Outflank Security Tooling (OST)
OST is a set of 20+ tools that perform things that red team members want to do.
These range from a Sharpfuscator (hides C# executables from AV/ERD), to Hidden Desktop (an OPSEC safe implementation of hidden Virtual Network Computing), to Stego Loader (embeds a payload in a picture file) and so on.
Several of the individual tools are discussed, with demos, click on this page.
The full set of tools is covered in this PDF, an OST summary sheet that you can download.
Learn about the powerful tools that are part of the Outflank toolkit.
Integrations with other Fortra solutions
OST was developed to work in tandem with Fortra’s advanced adversary simulation tool, Cobalt Strike and automated penetration testing solution, Core Impact.