Clearing and Endpoint Detection & Response (EDR) evasion – Cobalt Strike
Recently, a customer provided feedback that some EDR tools were detecting Cobalt Strike. The customer is a long-standing user of both Cobalt Strike and the Outflank Security Tooling (OST) suite. During our discussion, they raised a challenge that many penetration testers and red teamers will recognise: their Cobalt Strike deployments are being detected by endpoint detection and response (EDR) solutions more frequently than they’d like.
Clearing and EDR evasion – Cobalt Strike
In this post, I’ll share some of the insights, documents, and videos that we provide to customers to help them understand why this happens, and—more importantly—how to adapt their approach to stay ahead of detection.
We have divided up the sections below into sub-titles: Malleable Profiles, UDRLs, Static and Run-Time Evasion, and Post-Ex.
Malleable Profiles
- Malleable C2 Profiles
A Malleable C2 profile is a simple programme that modifies the behaviour of the Cobalt Strike Beacon.
This repository contains a set of Malleable C2 profiles aimed to help with the creation of your own. The best way to create a profile is to modify an existing one. Several example profiles are available in this repository.
https://github.com/Cobalt-Strike/Malleable-C2-Profiles
It is recommended to avoid defaults in the Cobalt Strike profile to improve evasiveness and mimic threats. You can modify things like:
- Avoiding using rwx
- How the process injection behavior works (which APIs will be used) in the process-inject section
- How the fork and run works in the post-ex section
- The default sleep time for beacons
- The max size of binaries to be loaded in memory
- The memory footprint and DLL content with stage section
- The network traffic
2. Cobalt Strike random C2 Profile generator.
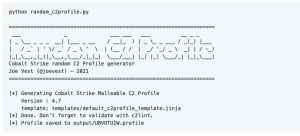
This project is meant to quickly generate a random c2 profile. It is basically a Jinja template with random variables. The idea is to focus on randomization vs a cohesive set of values that support a specific threat actor.
Detailed Malleable C2 profile information can be found at https://github.com/threatexpress/malleable-c2/.
3. Tylous/SourcePoint
https://github.com/Tylous/SourcePoint
SourcePoint is a C2 profile generator for Cobalt Strike command and control servers designed to ensure evasion. – GitHub – Tylous/SourcePoint: SourcePoint is a C2 profile generator for Cobalt Strike command and control servers designed to ensure evasion
UDRLs
4. Revisiting the User-Defined Reflective Loader Part 1: Simplifying Development – Cobalt Strike (UDRLs):
![]()
https://www.cobaltstrike.com/blog/revisiting-the-udrl-part-1-simplifying-development
The UDRL is an important aspect of Cobalt Strike’s evasion strategy. Cobalt Strike achieves “evasion through flexibility”, meaning they give you the tools you need to modify default behaviours and customise Beacon to your liking. As part of the blog post they created a Visual Studio project with several Quality of Life (QoL) improvements.
5. Revisiting the User-Defined Reflective Loader Part 2: Obfuscation and Masking – Cobalt Strike
https://www.cobaltstrike.com/blog/revisiting-the-udrl-part-2-obfuscation-masking
This is the second instalment in a series revisiting the User-Defined Reflective Loader (UDRL) exploring how to apply a customised obfuscation and masking.
As part of this post, CS have obfuscated, compressed, encrypted and encoded Beacon to evade a set of open-source static detections. Whilst this has demonstrated one approach, the post has shown that the possibilities are endless when developing your own custom obfuscation and masking routines within a UDRL.
6. Revisiting the UDRL Part 3: Beacon User Data | Cobalt Strike
![]()
https://www.cobaltstrike.com/blog/revisiting-the-udrl-part-3-beacon-user-data
The primary intention of this post is to demonstrate the UDRL’s role in runtime masking and show how Cobalt Strike’s two most important evasion tools interact.
Firstly it demonstrates how to track Beacon with BUD. Then after loading an External C2 DLL at the same time as Beacon and masking both DLLs at runtime with Sleepmask-VS. The UDRL and the Sleepmask are key components of Cobalt Strike’s evasion strategy, yet historically they have not worked well together.
7. kyleavery/AceLdr: Cobalt Strike UDRL for memory scanner evasion.
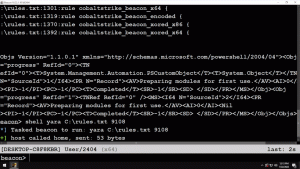
https://github.com/kyleavery/AceLdr
Cobalt Strike UDRL for memory scanner evasion, a position independent reflective loader for Cobalt Strike.
Static and Run-Time Evasion
8. Cobalt-Strike/sleepmask-vs: A simple Sleepmask BOF example – GitHub
https://github.com/Cobalt-Strike/sleepmask-vs
Sleepmask-VS has been updated to include BOF-VS as a submodule to simplify maintenance and development.
Therefore, “git clone” will not download all of the files required to compile the project.git submodule init and git submodule update are also required to initialize the repository and fetch BOF-VS.. Alternatively, “git clone –recurse-submodules <sleepmask-vs>” will instruct Git to initialize.
9. Cobalt Strike and YARA: Can I Have Your Signature?
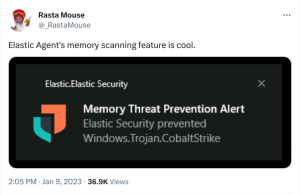
https://www.cobaltstrike.com/blog/cobalt-strike-and-yara-can-i-have-your-signature
Over the past few years, there has been a massive proliferation of YARA signatures for Beacon, that this has become problematic when using Cobalt Strike for red team engagements and that there has been some confusion over how Cobalt Strike’s malleable C2 options can help.
To demonstrate the power of YARA signatures you can use Elastic’s open-source rules for Cobalt Strike and run them against a default raw HTTP Beacon DLL (on disk).
As a note, this is a slightly contrived scenario, as typically when an exe/DLL is written to disk (or executed), an EDR will attempt to extract features and classify the binary via a PE malware model.
10. Introducing the Mutator Kit: Creating Object File Monstrosities with Sleep Mask and LLVM – Cobalt Strike

In the ‘Cobalt Strike and YARA: Can I Have Your Signature?’ blog post, it was highlighted that the sleep mask is a common target for in-memory YARA signatures. In that post it was recommended to use the evasive sleep mask option to scramble the sleep mask at run time and break any static signatures.
11. Dynamically Instrumenting Beacon With BeaconGate | Cobalt Strike

https://www.cobaltstrike.com/blog/instrumenting-beacon-with-beacongate-for-call-stack-spoofing
This blog demonstrates how to instrument Beacon via BeaconGate, and show how to implement return address spoofing, indirect syscalls, and a call stack spoofing technique, Draugr, that are now available in Sleepmask-VS.Furthermore.
Post-Ex
12. Cobalt-Strike/bof-vs: A Beacon Object File (BOF) template for Visual Studio – GitHub
https://github.com/Cobalt-Strike/bof-vs
This repository contains the Beacon Object File Visual Studio (BOF-VS) template project. You can read more about rationale and design decisions from this blog post. The Debug target builds your BOF to an executable, which allows you to benefit from the convenience of debugging your BOF code directly.
Besides that, using BeaconBooster and the Payload Generators (Builder and PE Payload generator) could make their life easier as they can accelerate the generation of those artifacts.
If you have any more comments to add, questions, or feedback on Cobalt Strike, OST or any other Fortra products, please use the “Contact” form, and we would be happy to hear your thoughts or challenges.

