Background
Businesses the world over are facing a growing threat of cyber-attacks, with the number of incidents increasing year-on-year in both scale, complexity and impact.
One of the major ways that criminals attack businesses is by using ransomware to encrypt files stored on a computer and hold them for ransom to extort money.
The files are encrypted, ‘scrambling’ the contents so that they are unreadable to the owner. To restore the files so that they can be used – a decryption key is needed to ‘unscramble’ the files.
This type of ransomware takes the files “hostage”, and demands a ransom. Typically payment must be made in Bitcoin or other crypto-currencies in exchange for the decryption key needed to restore the files.
So, how did this all start?
Computer viruses have been around for a long time, here’s how they got going …
The first computer virus, called “Creeper system“, was an experimental self-replicating virus released in 1971. It filled up the hard drive until a computer could no longer operate. This virus was created by BBN technologies in the US.
Before the Windows operating system, MD-DOS based PCs used floppy disks. The first computer virus for MS-DOS was “Brain” and was released in 1986. It would overwrite the boot sector on the floppy disk and prevent the computer from booting.
“The Morris” was the first Computer virus which spread extensively in the wild in 1988. Written by Robert Morris, it spread quickly and interfered with the limited number of computers that were operating on the internet at that time.
Evolution of viruses
Viruses initially started out as complex pieces of code, written by very clever people, in essence to show off to other very clever people. Normal users and businesses were just collateral damage in this “arms race” to show who was the smartest at writing code. If someone was to boast that they had infected 1 million computers, then they had to get 1 million people running their code / programs.
The virus didn’t usually do anything other than spread itself further. It had no / very little impact on the machine running it.
By the early 2010’s there was a transition to viruses created for criminal gain, people wanted to make money rather than just show off. This started with viruses popping up annoying ads on your computer, but this didn’t generate much money.
Then cyber-criminals progressed to stealing data, everything from credit card details to sensitive healthcare information. This allowed them to earn significantly more.
Read our blog Best Practice Steps for Effective Vulnerability Lifecycle Management
Show me the money …
Although cyber-criminals had up until this moment in time been able to generate money from selling data, they could not by-pass the traditional banking systems, which meant that their actions could be traced.
In addition, hacking was a lot of effort, requiring human intervention to search through a compromised computer looking for valuable files. These human interactions limited the scope, scale and volume of cyber-attacks they could execute.
For more on how to assess your security posture, read our blog: Assess your security Posture with our Security Maturity Model.
What is Ransomware?
Ransomware is made up of 3 technologies, combined for devastating effect:
- Some form of attack to get a machine to run the ransomware code
- Off the shelf encryption technology
- Untraceable payments (think crypto-currencies)
Step 1 – get the machine to run something
Hackers had been doing this bit for ages, with their viruses. Sometimes the users don’t need to do anything (aka WannaCry), other times they have to take an action (click on an email link, down-load a file, etc).
As the years have gone by, operating systems have gotten better, so there are fewer and fewer vulnerabilities left that can just run code without users doing anything.
This leaves email as the most common way for ransomware to compromise a computer, clicking a link or downloading a file from an email that appears to be genuine.
Step 2 – use encryption
Mathematicians long ago worked out how to make encryption that cannot be broken, the only way to de-crypt a file is with the key.
So once step 1 has been achieved the code will look around the users machine and network connected devices, it will then encrypt all of the data files, Word document, Excel files, pictures etc.
Step 3 Untraceable payments
Once everything has been encrypted the software would pop up a screen and say “Send X bitcoins to this account number, and we will give you the decryption key”.
If you followed the instructions, then you would get the key, enter it into the screen on your PC, and it would then decrypt everything as promised.
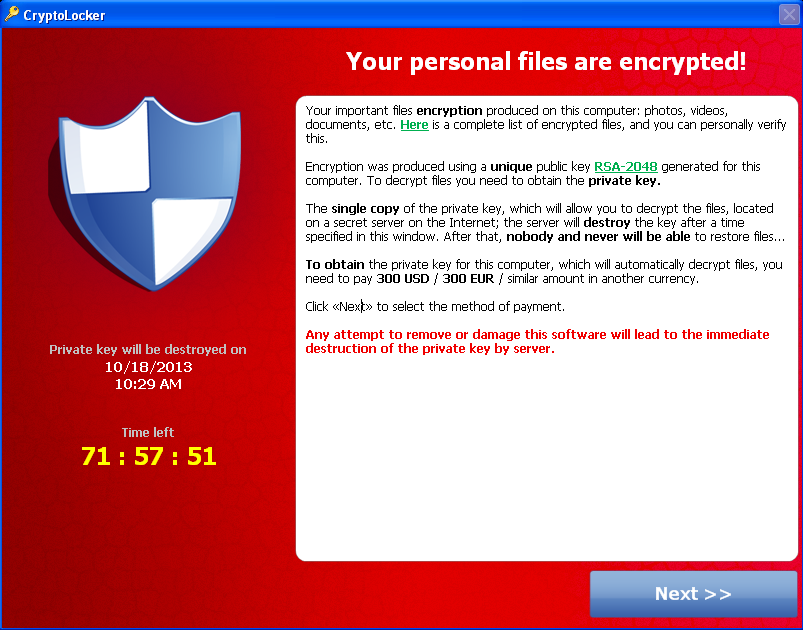
The first Ransomware, V1.0
It wasn’t until 2013 that the first real form of ransomware was introduced called CryptoLocker. This was completely automated, and would charge about $300 – 500 for a decryption. From mid October to mid December that year CryptoLocker earned cyber-attackers about US$ 27M.
EternalBlue is a cyber-attack exploit developed by the U.S. National Security Agency (NSA) and was leaked by the Shadow Brokers hacker group in April 2017.
Although Microsoft released a patch for this vulnerability, many systems worldwide were based on old versions where the patch was not available, or just had not had the patch applied. This allowed the WannaCry ransomware to gain a strong foothold, infecting around 200,000 computers across 150 countries in 24 hours.
Upping their game …
Companies often mistakenly think that they are too small to be on the radar of hackers and cyber criminals – but these criminals are opportunists.
The majority of cyber-attacks are not planned or highly targeted. They are automated and indiscriminate, exploiting known vulnerabilities within commonly used IT systems, 24/7.
Cyber-attacks can be devastating for a business, causing considerable financial and reputational damage. Ransomware has become the ideal tool for criminals, because it can be 100% automated.
What do crypto-currencies add?
Bitcoin has been the most high profile of crypto-currencies, invented in 2008, it entered circulation in 2009 and is the first, and most famous of over 100 different crypto-currencies available today.
For this discussion, consider that bitcoin provides everybody with a numbered bank account. That is all that is needed to make a transaction, the bank account number. Nobody knows who is behind that number. If you want another number you can get one by just running some software.
Once you have the bank account number you can then say to anyone, “here is my bitcoin account number, send me some money”. When they carry out the transaction it is easy to see the money enter your account.
There is no information anywhere other than the bank account number and the balance. You don’t even know which country the crypto-currency account was generated in.
This anonymity is what drives bitcoin’s popularity, and also makes things difficult for law enforcement agencies to make any investigations.
It is crypto-currencies that enable the 3rd step. The cyber-criminals couldn’t say “Here is my HSBC bank account please send $500”, because that transaction would be tracked and traced in an instant. So, without it you would need to meet the victim in person to collect cash. This would be viable if they were doing very large transactions, but for $500 it’s not worth the effort for the cyber-criminals.
Ransomware version 2.0
Cyber criminals, like most successful criminals, are smart, very smart. They worked out that for a user wanting their family pictures back then $500 is about right. For a large corporation though, that is peanuts, so they have segmented their business into B2C (business to consumer) and B2B (business to business).
For the larger, more profitable B2B businesses they have more resources invested in the process. If they get into a corporate network they will look around, find out where the backups are kept, and before encrypting anything, they will delete the backups and take a number of other steps that make it hard for the business to avoid paying the ransom.
In the same way you get Software as a Service (SaaS), there is now Ransomware as a Service (RaaS) offered by a number of crime syndicates.
As a prospective hacker you’ll receive the necessary code to run the RaaS, the services provided include:
- Encrypting everything for you
- Managing the ransom demand and collection in crypto-currencies
- Decrypting everything for the client
- Pass you the proceeds, minus their “commision”
As the prospective hacker you just then need to get someone to run the code, as per step 1 above. Everything else is taken care of for you.
These RaaS groups take professional pride in their work, patching any loopholes in the encryption logic so that there is no way of decrypting without paying the ransom.
Recently they have gone 1 step further, by extracting the company data before encrypting. When they make the ransom they then offer 2 options:
- Pay the ransom in full and get the decryption key, they will delete their copy of your data that they hold
- Pay a smaller ransom, they will delete their copy of the data that they hold leaving the company to recover the encrypted data by other means, for example from a backup
If you decide against paying the ransom, then they will gradually release the sensitive information into the public domain to embarrass you or your company.
Next steps
In order to remain one step ahead of these cyber-attackers, it’s important to audit your security posture regularly, especially if you have seen a surge in attacks in your industry.
Better that you know your weak spots before a hacker does.
Read more about risk based vulnerability management with our Brinqa case studies, learn more about Brinqa or contact S4 Applications to request a demo.
To learn more about vulnerability management, read out blog: Staying safe with Risk Based Vulnerability Management.


